Exciting things are in store for Azure DevOps in the coming year! We’re planning deep investments in security as well as broad investment across the product. Read on for more information, and then be sure to check out our updated roadmap at https://aka.ms/AzureDevOpsRoadmap.
Deep investments in security
First, we are super excited about bringing GitHub Advanced Security and Microsoft Defender for Cloud’s new Defender for DevOps capabilities to Azure DevOps customers! Additionally, two other major security initiatives are planned for Azure DevOps over the coming year. The first is focused on minimizing the risks associated with credential theft; the second, on making it easier to harden Azure DevOps organization configuration.
GitHub Advanced Security
Customers using Azure Repos and Azure Pipelines have up to now been unable to take advantage of GitHub Advanced Security’s industry leading capabilities. We’re pleased to announce that GitHub Advanced Security for Azure DevOps will bring these capabilities to Azure DevOps, natively integrated into Azure Repos and Azure Pipelines. This brings the same secret scanning, dependency scanning, and CodeQL code scanning capabilities of GitHub Advanced Security right into the Azure DevOps environment that these teams are already familiar with.
- Secret Scanning: Exposed credentials are implicated in over 80% of security breaches. GitHub Advanced Security for Azure DevOps can not only help you find secrets that have already been exposed in Azure Repos, but also help you prevent new exposures by blocking any pushes to Azure Repos that contain secrets.
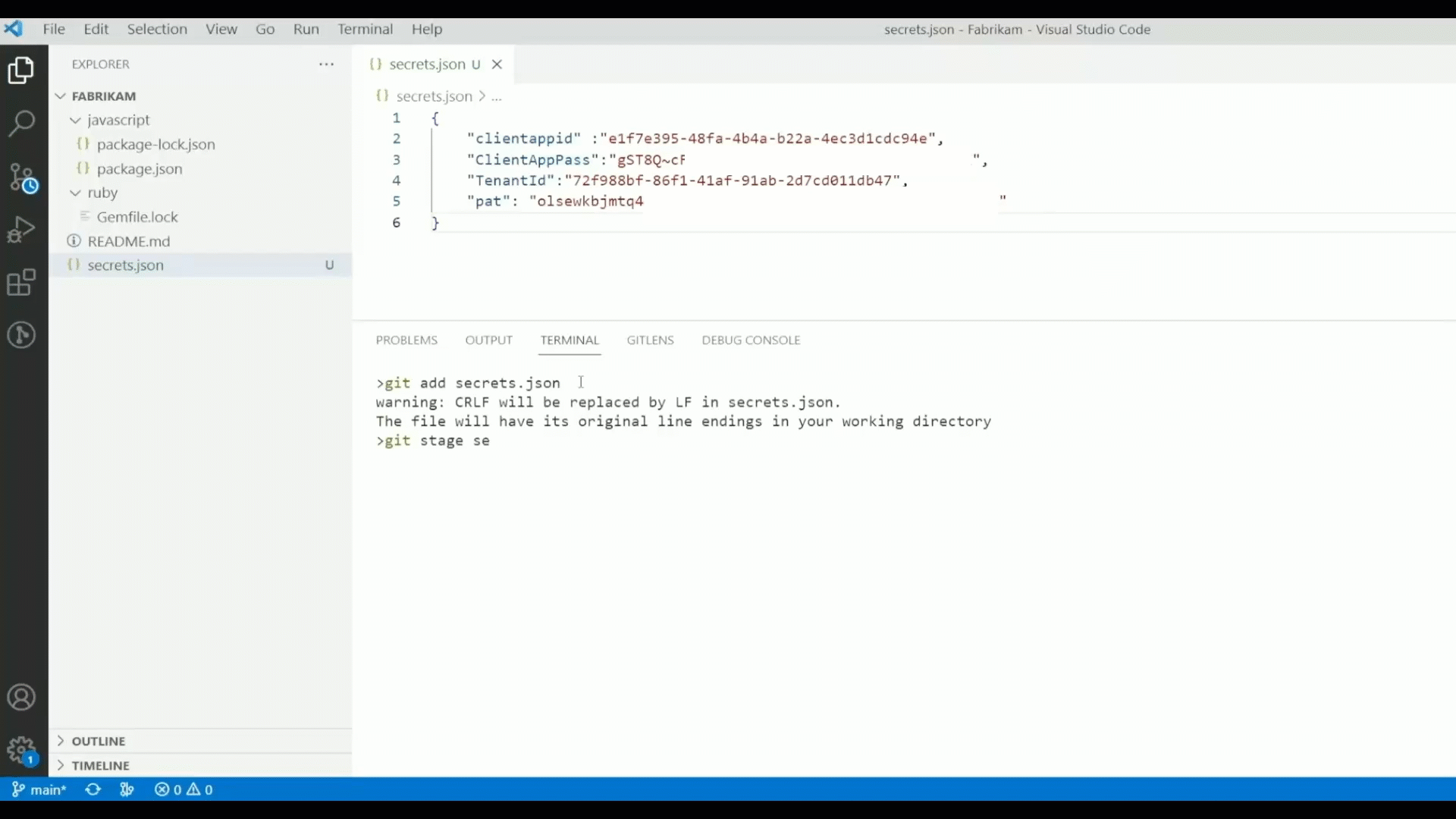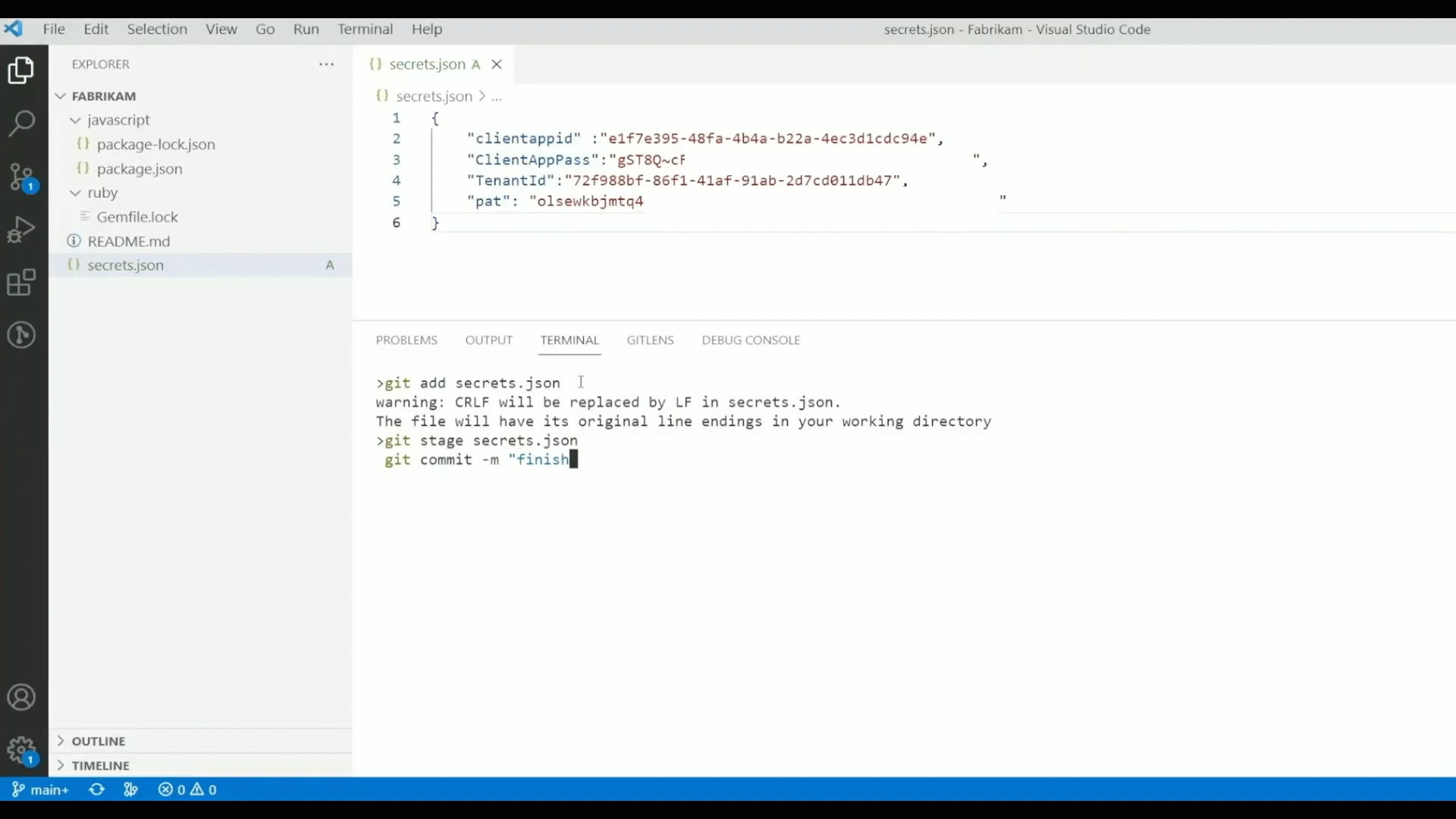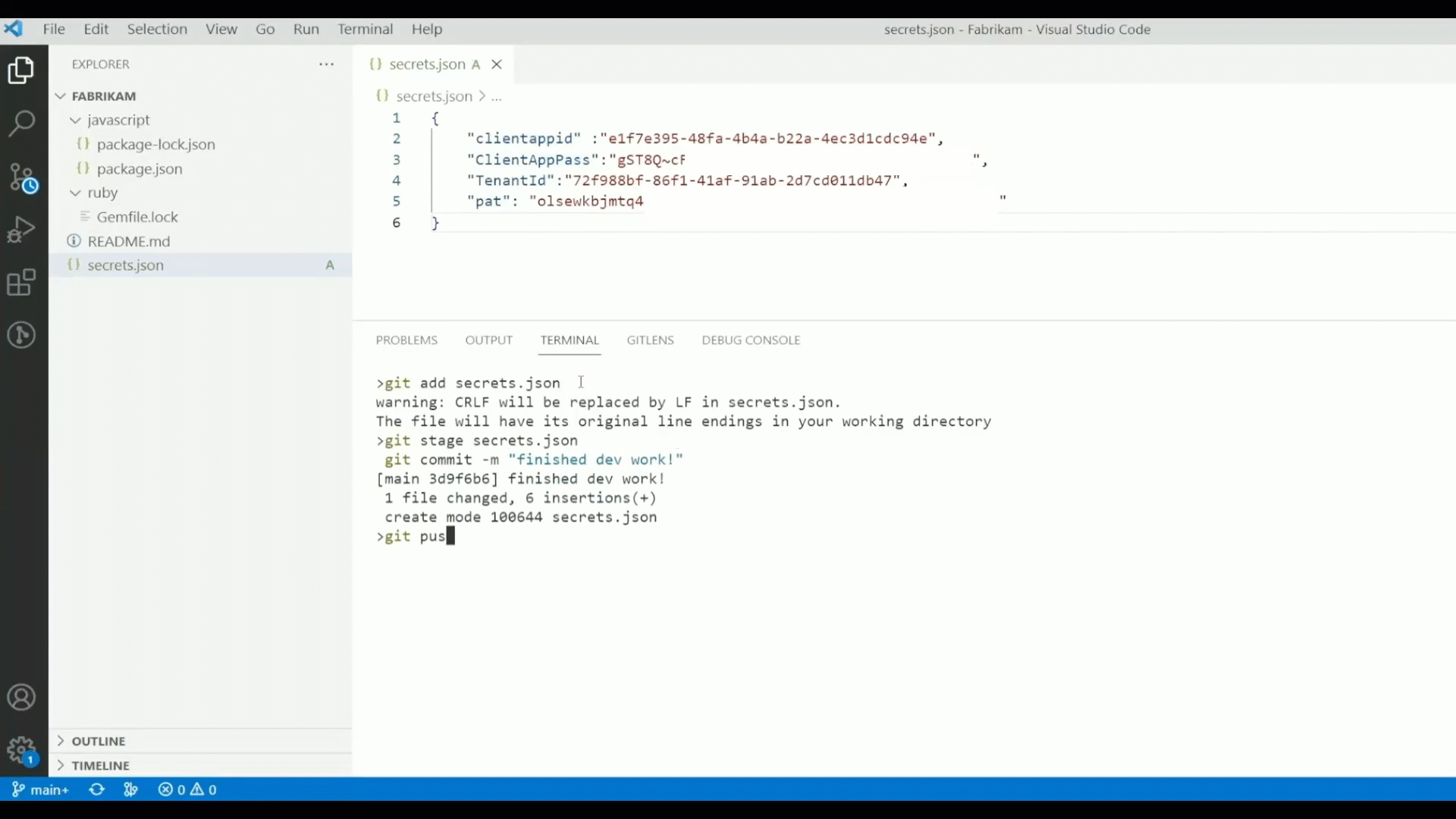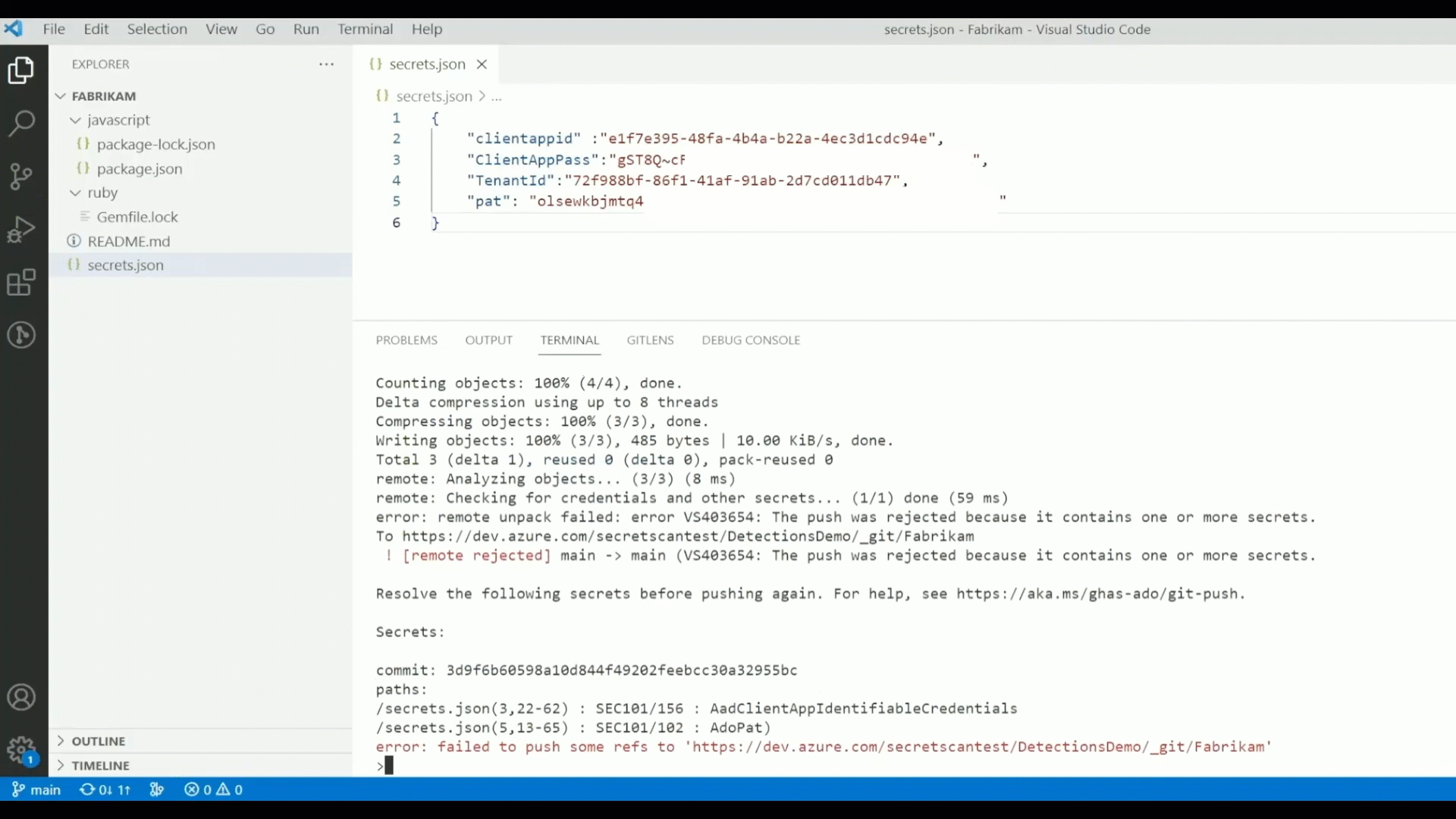
- Dependency Scanning: Open-source supply chain attacks such as the “Log4Shell” incident are on the rise. GitHub Advanced Security identifies the open-source packages used in your Azure Repos – both direct and transitive dependencies – and provides straightforward guidance from the GitHub Advisory Database on how to upgrade those packages to mitigate vulnerabilities.
- Code Scanning: GitHub Advanced Security uses the industry-leading CodeQL static analysis engine to detect hundreds of code security vulnerabilities such as SQL injection and authorization bypass across a wide range of languages including C#, C/C++, Python, JavaScript/TypeScript, Java, Go and more. GitHub Advanced Security for Azure DevOps enables you to run CodeQL scans directly from Azure Pipelines on code from Azure Repos and act on the results without ever having to leave your Azure DevOps environment.
GitHub Advanced Security for Azure DevOps will ship to limited private preview customers in early November 2022. To be considered for future preview programs, please visit https://aka.ms/advancedsecurity-signup.
Defender for Cloud
In addition to helping developers find and fix vulnerabilities by integrating alerting and remediation guidance directly into the Azure DevOps experiences they already use every day, GitHub Advanced Security will also integrate with Microsoft Defender for Cloud’s new Defender for DevOps capabilities to empower security managers and leaders to unify DevOps security posture visibility across multiple pipelines and help strengthen security from development to runtime.
Minimizing risks from credential theft
Azure DevOps supports many different authentication mechanisms, including basic authentication, personal access tokens (PATs), SSH, and Azure Active Directory access tokens. These mechanisms are not created equal from a security perspective, especially when it comes to the potential for credential theft. For example, unintended leakage of credentials like PATs can let malicious actors into Azure DevOps organizations where they can gain access to critical assets like source code, pivot toward supply chain attacks, or even pivot toward compromising production infrastructure.
Over the past year, Azure DevOps has been investing in strengthening protections around the usage of PATs, including Azure AD-Tenant-scoped policies around allowable PAT scopes and lifetimes; APIs to help automate PAT creation, revocation, and rotation; and association of all Azure DevOps APIs with appropriate PAT scopes to minimize the need for “full-scoped” PATs with no limitations on their use beyond the permissions of their underlying user.
Beyond these efforts to reduce the risk of PAT usage, we are also focused on reducing the need for PATs in the first place. An example of this is the work we did with our partners at GitHub to enable support for Microsoft identity OAuth tokens in Git Credential Manager (GCM) when connecting to Azure Repos repositories. Up next is support in Azure DevOps for Azure Service Principals and Managed Identities to reduce the need for PATs in application integration scenarios. Service Principals offer several security benefits beyond PATs – when used with Certificate authentication, their secrets cannot accidentally be embedded in code; they can be stored in Azure Key Vault and optionally auto-rotated; and so forth. Managed Identities go a step further by removing the need to manage secrets altogether.
Similarly, while Azure Pipelines today support secret-free deployments into Azure using Managed Identity service connections from self-hosted agents, Microsoft-hosted agents are limited to using Service Principals – often with client secrets rather than certificates. These secrets are comparatively easy to steal, and therefore must be protected, rotated, and so forth to ensure they do not become an attack vector. We’re working now on support for secret-less deployments from Microsoft-hosted agents that leverage federated credentials using OpenID Connect (OIDC), similar to the capability that exists today in GitHub Actions.
Longer term, we are deepening our integration with Azure Active Directory (Azure AD) and embracing Azure AD access tokens as the primary authentication method in Azure DevOps. This will enable us to better support a variety of security controls provided by Azure AD such as Conditional Access Policies, proof of possession to prevent token theft, and continuous access evaluation to respond more quickly to policy violation and security issues. As part of this, we’ll also provide a set of new policies and controls to help reduce and eventually phase out the use of less secure authentication mechanisms.
We’ll adopt all these security investments within Microsoft along the way, both to better secure our own assets and to help ensure we make the transitions and adoption as simple as possible.
Hardening Azure DevOps organization configuration
Over the past couple of years, we’ve introduced many new security-relevant configuration settings. While we’ve always followed “secure by default” principles and enabled these settings for newly created organizations/projects, we’ve not enabled them for existing organizations/projects to avoid disruptive impacts.
For example, we’ve introduced several improvements to the security posture of Azure Pipelines, including restricting the default scope of the pipeline identity from the entire organization down to the project, restricting the resources that can be accessed by a pipeline to those which it explicitly references, and more. Collectively, these changes prevent malicious actors from using pipelines to move laterally within an organization and gain access to resources to which they personally lack permissions. These settings are all enabled by default in new organizations and projects. But because enabling them in existing organizations and projects can cause existing pipelines to start failing, we’ve left it to administrators to explicitly enable them.
We’ve listened to feedback from security-focused customers and Azure DevOps administrators, and we’ll be focusing on making it easier for them to:
- Understand the recommended state of all the various settings within Azure DevOps,
- Find all the settings which are not in their recommended states, and
- Adopt the recommended settings while minimizing disruptive impacts within their organizations.
We’ll start by ensuring that security-relevant settings all have clear recommendations in the product. Longer term we’ll focus on enabling non-disruptive rollout of configuration hardening through audit modes, allow lists, and auto-mitigations. For the Pipelines settings discussed above, these changes will allow administrators to understand which settings are not in their recommended states and which pipelines will start failing when the settings are updated. Further, they will allow pipeline owners to easily understand and apply the changes required to keep their pipelines working.
Broad investments across the product
In addition to these deep investments, we’ll also be making broad investments across all areas of Azure DevOps, focused on feedback and feature requests from our top customers.
In Azure Pipelines, we’ll be focused on three initiatives – service connection security, including the OpenID Connect work described above and multiple smaller items; YAML deployment improvements, including lots of work related to Checks; and dependency refreshes, including upgrading our agents to .NET 6 and upgrading our task runner to newer versions of Node.js (and laying the groundwork to keep up with the Node support lifecycle moving forward).
In Azure Boards, we’ll be focused on bringing the New Boards Hub (a refresh of the Boards user experience that brings improved performance, improved support for mobile browsers, improved accessibility, and a bunch of features that have shipped over the past several months) to general availability. Along the way, we’ll continue delivering a steady stream of feature requests and experience improvements, including support for markdown fields, swimlane rules for Kanban boards, and more.
In Azure Test Plans, we’ll be reinvigorating our investments in manual and exploratory testing scenarios, starting with improvements to pause/resume functionality. In automated testing space, we’ll be focused on improvements to code coverage capabilities.
In Azure Artifacts, we’ll be focused on expanding our support for additional protocols, beginning with support for the Cargo package manager for Rust. We will continue to invest in the security and reliability of the packaging platform so we have the right infrastructure to support a broader range of protocols. In the next 6 to 12 months, we plan to add native support for additional protocols based on the prioritized asks from customers.
For more detail on all this and other investments across the rest of the product surface area, check out our updated public roadmap at https://aka.ms/AzureDevOpsRoadmap.


I’m especially excited to see the secrets scanning added in. I’m eager to see many of these enhancements but secrets scanning is a real value add!
We are planning to move Azure devops pipelines to Github actions by Dec-2022 to leverage Github Advance Security for SHIFT LEFT security in SDLC. When will be the proposed integration between Azure DevOps and Github live for users? I don’t see tentative timelines in your product roadmap
Hi Vaibhav, are you by any chance using Azure Pipelines to build code stored in GitHub repos? If so, unfortunately GHAS for Azure DevOps won’t apply to this scenario, because GHAS for Azure DevOps works to protect Azure Repos only. If you’re using GitHub for source control, GHAS for GitHub will be your best option.
Hi Bryan, Thank you for your response. We are using Azure pipelines for CI-CD and Azure TFS as code repositories for internal custom web applications. Can you please elaborate on what shall be our next plan.
“We’re planning deep investments in security as well as broad investment across the product.” Great news, because we use a lot custom work items, boards features, query features, power bi reporting.
You need to improve the wiki, or integrate with Microsoft Loop in the future.
Cost?
Free in Preview for now at-least
Hi Team,
I am trying to connect GitHub enterprises to azure devops cicd pipeline. While connecting pipeline repositories not showcasing.
Can some expertise can help me out.
Thanks you
Blog comments aren’t the best place to look for this kind of support, Sivakumar. Suggest you review docs, check Developer Community, file a support ticket, etc.
Very excited by the GitHub Advanced Security features but I couldn’t see them anywhere in the roadmap. Are they under a different heading there?
Thanks for bringing GHAS integration with Azure DevOps Services!
I have two questions :
– how this service will be billed?
– will we have a view like in GitHub to see stats about vulnerabilities accross the organization?
Hi Kevin, we’re still working out billing details for GHAS for Azure DevOps, but please see this info on billing for GHAS for GHE.
For a security overview, what kind of stats would be most useful to you? How would you use them? I’d love to get your insights here, and I’d be happy to take this conversation to email if you’d prefer. Thanks!
Hi Bryan,
Thanks for your answers!
Yes, it might be easier if we could communicate by e-mail about what are we looking for.
Really cool changes coming. Thank you.
Looks like risks with PAT usage is finally on roadmap. Nice work.
Sadly, Azure CLI extension login process is really flaky and the recommended solution is to use PATs. I already posted proposal of the fix on Github https://github.com/Azure/azure-devops-cli-extension/issues/1298 but it has not got any public feedback or discussion.
I also recently found out that permission management of the environments is really weird not having feature parity with other Azure Devops features:
* Looks like it is impossible to assign admin rights on project level for enviroments
* all other features like variable groups, deployment...
Thanks for that feedback, Janne. We’ll take a look.
I read about the changes to permissions but I don't know that it addresses the concerns we have. The existing permissions in DevOps are too broad, very difficult to track and nearly impossible to manage across more than 1 or 2 repos. We have over 80 repos and we bring in consultants to work on certain projects. Setting up the permissions for these folks is an absolute nightmare and there is no way to know you've gotten it right. For example I want to be able to ensure they only have permissions to view the repos I want them to...
Hi Michael, I understand your pain. In addition to the response from Aaron, I can add that there are ways to organize permissions in a better way in Azure DevOps. I wrote a blog on how to do that. You can find it here: https://veegens.wordpress.com/2021/07/19/enterprise-level-azure-devops-permissions-from-the-trenches/. If you have any questions, feel free to contact me.
"The existing permissions in DevOps are too broad, very difficult to track and nearly impossible to manage across more than 1 or 2 repos."
That's good feedback Michael, thank you. Over the years we've have many requests for "more granular" permissions in Azure DevOps so that customers can pick and choose what groups and individual users are allowed to do, and it has certainly led to a system that, while quite powerful, can be difficult to use. We could and should do more to make it simpler.
"Even if we set up a separate project in the same org they still have...
This sounds great! Will it be available for on prem Devops?
No, we are not planning to bring GitHub Advanced Security for Azure DevOps to Azure DevOps Server.
tl;dr: It's a prioritization decision.
The vast majority of the Azure DevOps customer base is in our hosted service now, not on-premises, with many of our customers having migrated using our high-fidelity data migration tool. We expect that trend to continue (and actively encourage customers to migrate to our hosted service). As such, the benefit (in terms of number of customers served) of doing the work to bring net new services to Azure DevOps Server is comparatively low and declining over time. Meanwhile, the costs of doing this work are non-trivial, given the substantial differences between the two flavors of the...
Thank you for in-depth clarification here, Aaron. This clarification is something we can certainly take to other customers if we are asked, as administrators of Azure DevOps Servers, as to why this prioritization decision has been made.
Thank you again
Thank you Aaron, This is some good clarification for those still using Azure DevOps Server / those managing on-premises platforms.
With the advent of products like Microsoft Arc, is the absence of the plan to bring it to Azure DevOps Server a decision or simply not part of the plan?
I am specifically asking for other customers that might be curious for GitHub Advanced Security finding its way to on-premises platforms.
Thank you
Why not?