Developer Best Practices – YAML Exposure in your pipeline
As a good developer, I have my code in a repo, that doesn’t necessarily mean that I have followed all of the best practices that I should. I can still expose myself to risks unknowingly.
I’ve been working with Azure Static Web Apps for many months now, and they’re awesome! Often in tutorials or getting started guides, we try to make the code and directions as easy as possible for anyone to be able to follow. While this is great for the community, sometimes while we make things easy to get started, but do not consider the impact it can have on the consumer. Meaning, I have deployed my Azure Static Web App, but exposed myself to what could a potential security risk for myself or my organization. In hindsight, we need to make sure our tutorials are fit for purpose and production.
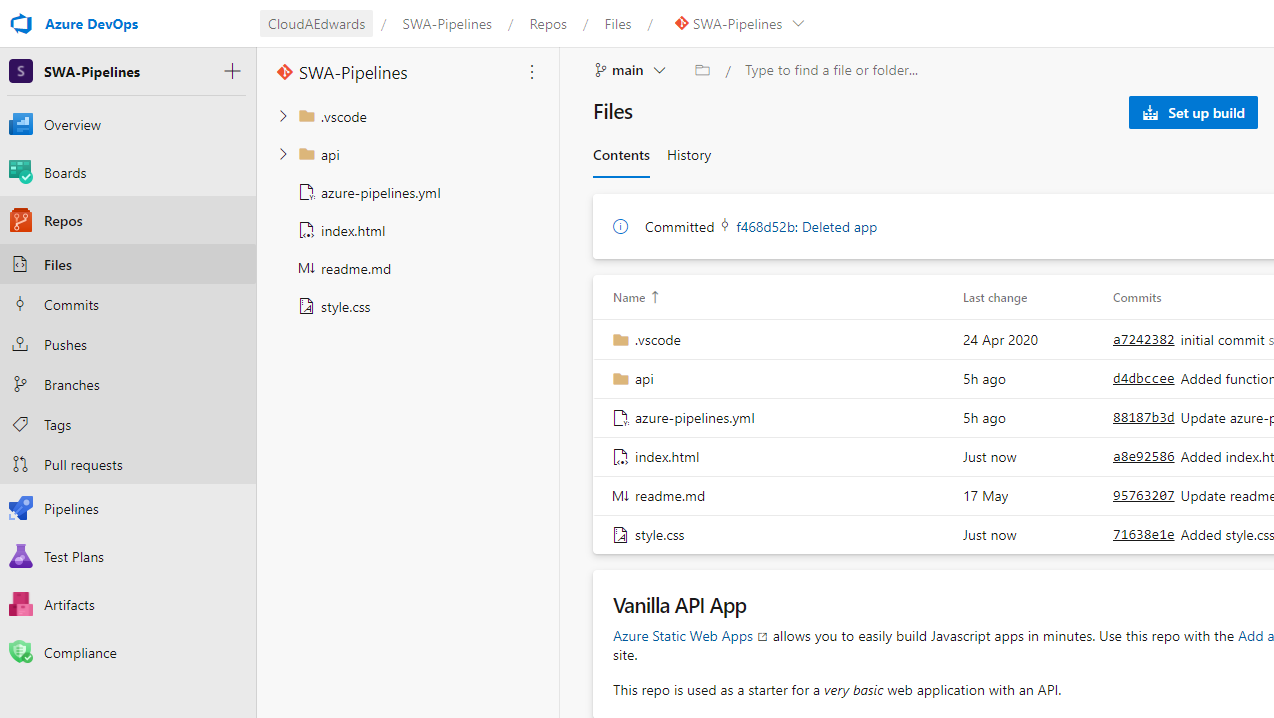
In the tutorial, I have a very simple repo in Azure DevOps where I keep my code. I want to deploy my Azure Static Web App using a simple repository, which I walk you through in this tutorial. The tutorial is easy to follow and aims to get people started on their DevOps journey, so we really want to start with a simple version of code. Many will bring their own code, or maybe start with this super simple repo. In the tutorial I started with a very basic, vanilla build, if you will. I copied the repo, deployed my static web app and had a full CI/CD pipeline up and running within minutes.
As a developer, we should ALL care about security. We want to ‘shift left’ and implement security early. While nothing obvious sticks out, I don’t have any exposed secrets in my YAML, I’ve done all the things right. But wait.. I haven’t. I dare you as the reader to look at my repo and see what I exposed? Find it yet?
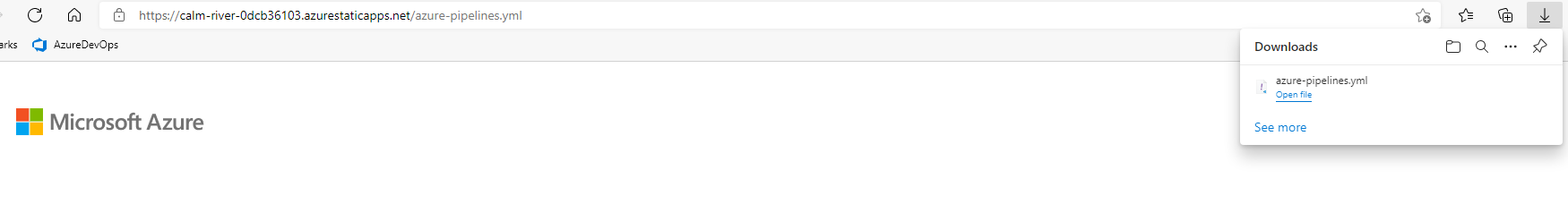
Answer: I deployed my app from the root of the folder. When Azure DevOps created the pipeline and I wrote my YAML, it was also exposing all files in the root folder. I found that I can browse to that YAML file publicly. OOPS!
While I have protected my secrets following all of the best practices, what if I hadn’t? What if another developer in the team hadn’t? We deployed our Azure Static Web App and could have potentially exposed critical information externally.
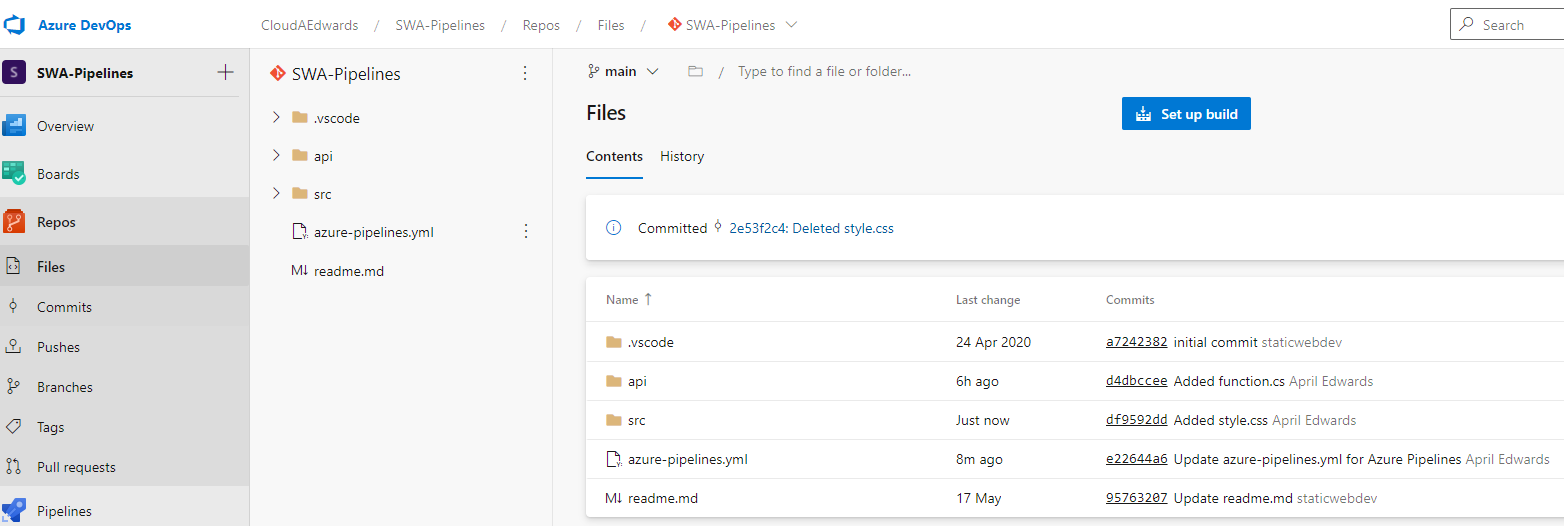
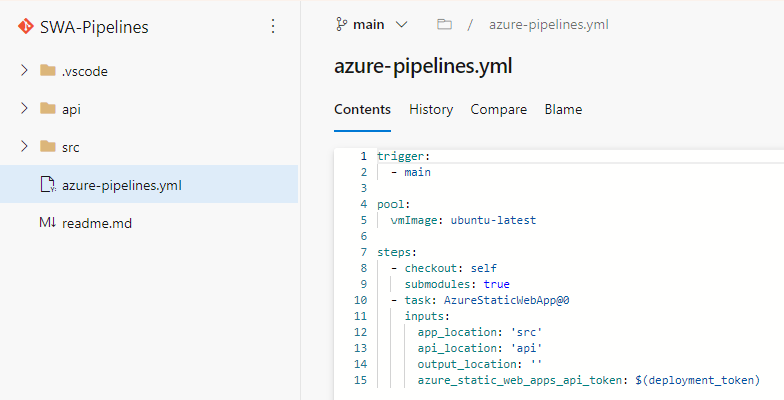
How did I resolve this? I created a new folder named ‘src’, moved my application files to that folder, instead of the root folder. This is simple as a ‘create a new folder’ and copy/paste the files.
One last thing, I need to change my ‘azure-pipelines.yml’ file to find the correct folder of my app:
My code gets checked in, the CI/CD process runs and redeploys my app from the folders specified. I now can no longer access the YAML file from the root folder. I also opened up an issue on the repo that I used so that others don’t make the same mistake, even better than that, the owner of the repo has also updated the repo to fall in line with securing the files.
Another way to do this would be to exclude files in the static web app pipeline task. While that currently isn’t a feature, that should be coming soon. No matter what resources you are deploying in Azure, be aware of your repo configuration and start thinking about your external exposure and risks to your environment.
If you want to get started learning via an interactive tutorial, check out one of the Microsoft Learn modules for Azure Static Web Apps.

0 comments