Most organizations today consume open source software in their development projects. The reuse of components enables great productivity gains. However, this practice has an unintended consequence: you can reuse security vulnerabilities or violate licenses without realizing the risk. I wrote about this in an article in MSDN Magazine on Rugged DevOps.
For users of VSTS, there is now a great extension to help discover and remediate the risk: WhiteSource Bolt is now available in the marketplace. WhiteSource, an open source security & management platform provider, has been working with Microsoft to offer an integrated solution within the VSTS product, so that you can scan components directly from your build and release pipeline. TFS support is coming soon.
When you install the Bolt extension, it is ready to use in trial mode. I found that I could add the build task with no parameter configuration and run the component scan successfully on first try. It’s an extraordinarily easy flow.
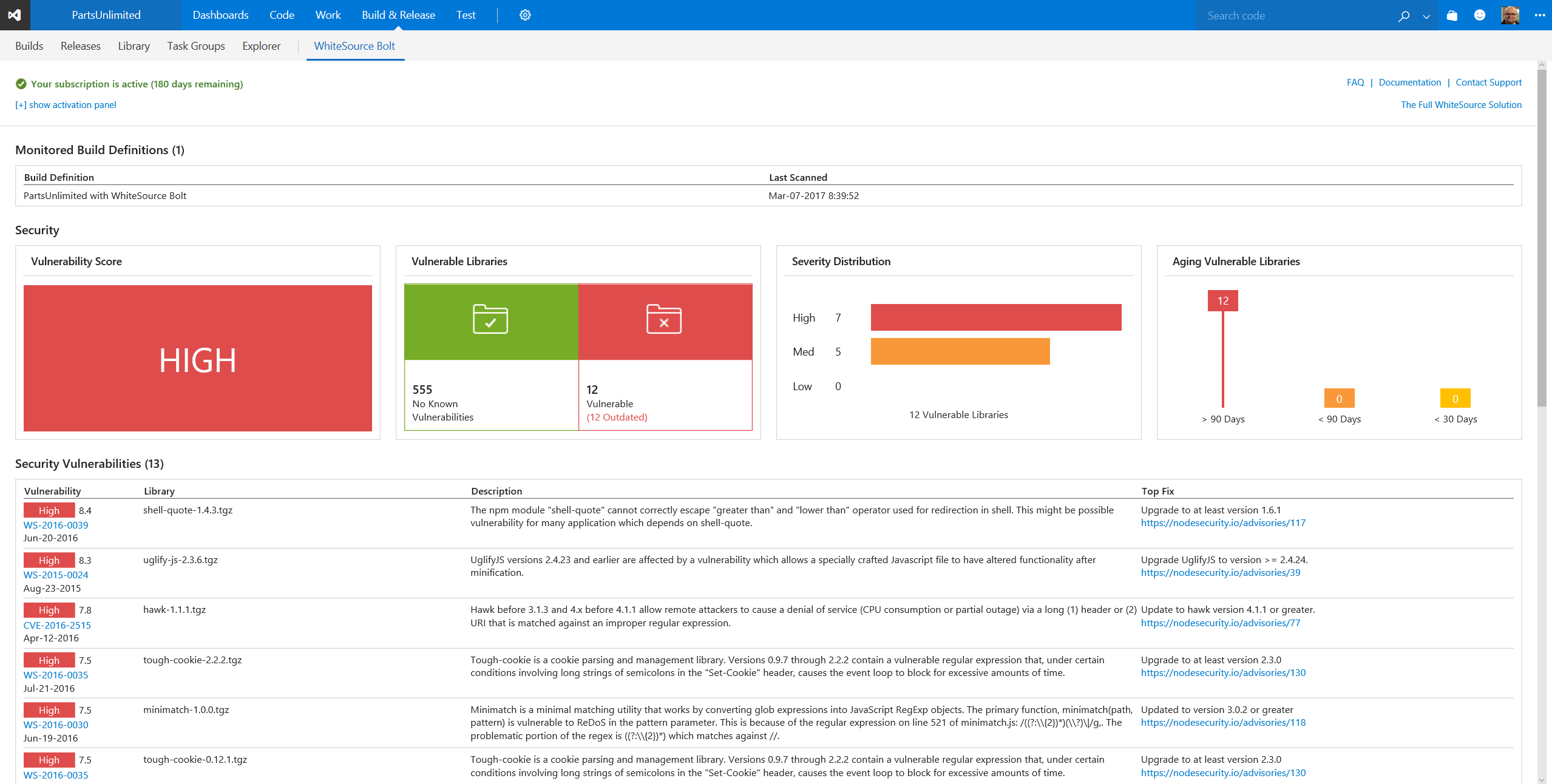
You add Bolt as a build task, save and queue the build and then you have a report on vulnerabilities and licenses that looks something like this:
There are a few things to note about this report. In the table under the summary, you see each vulnerable component listed. On the left is a hyperlink to the source information about the vulnerability. On the right, for each component, is a link to the most recommended fix.
If you’re a security geek, you’ll probably note that of these seven high-vulnerability components, only one is enumerated in the National Vulnerability Database (as CVE-2016-2515). WhiteSource identifies the other six from its own security research.
If you have Visual Studio Enterprise , you now get 6 months use of WhiteSource Bolt for one team project included with your subscription. You can redeem a code from your benefits page. WhiteSource has posted a page for VS subscribers with more detailed instructions..

0 comments