We previously talked about GitHub Code Scanning capabilities which enabled developers to incorporate security checks into their CI/CD environment and developer workflow. CodeQL is the default analysis engine behind Code Scanning. Today we are introducing support for MSVC Code Analysis which will provide a great companion to CodeQL for C++ GitHub repos with Windows workflows.
This Action will take the variety of Code Quality and Security warnings available in Visual Studio today and process them as alerts, displaying them in the Security view of a GitHub repository. The code scanning alerts produced will power the existing features available through GitHub. These include highlighting the source code of contributors’ PRs with any warnings they may have introduced or allowing repository owners to view and manage the backlog of alerts under the Security tab.
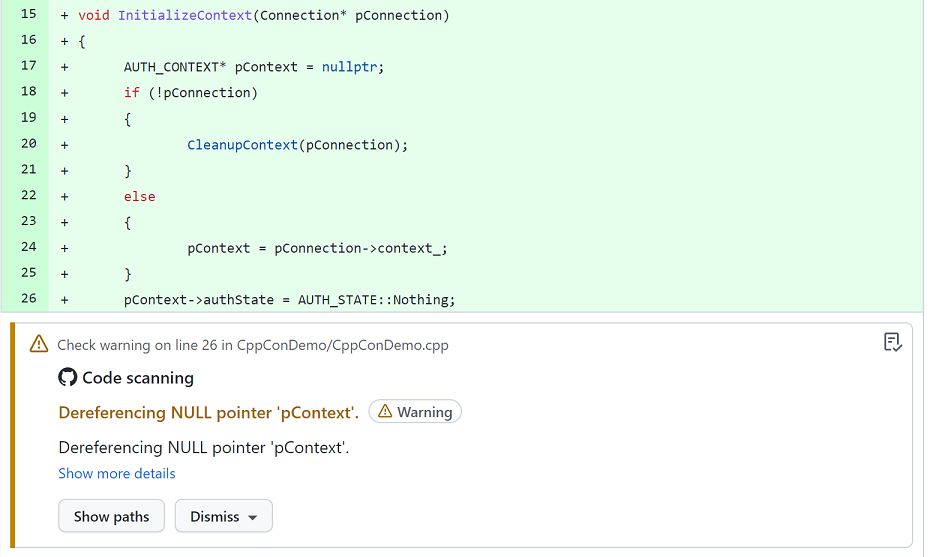
Alongside the support for analysis alerts inside of GitHub, the results can also be published as workflow artifacts, allowing contributors to download and view them locally in the IDE. This is enabled by our support for SARIF, which is a standardized file format for analysis tooling. This format can be viewed inside of Visual Studio Code using the SARIF Viewer extension. This will provide additional information highlighted on the source code, allowing the developer to easily resolve any problems found.
The repository will need to support CMake to ensure information about how the project is built can be extracted. We chose CMake because it provides a good abstraction for the varied nature of C++ projects and due to its wide adoption in the open-source community. It also provides an easy path for teams not currently building with the Microsoft Compiler to get analysis setup and see the features it has to offer.
Setup GitHub Action
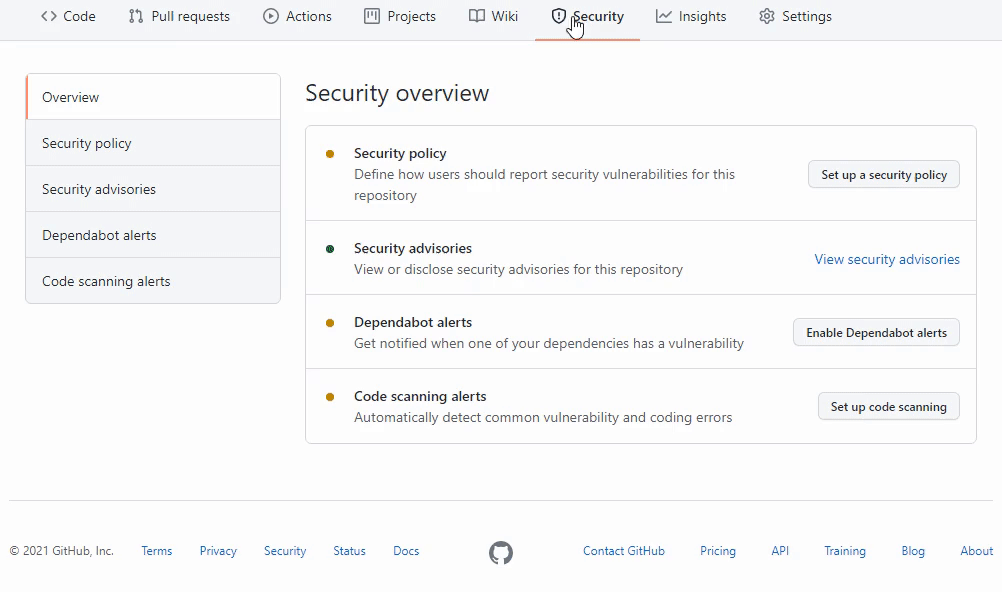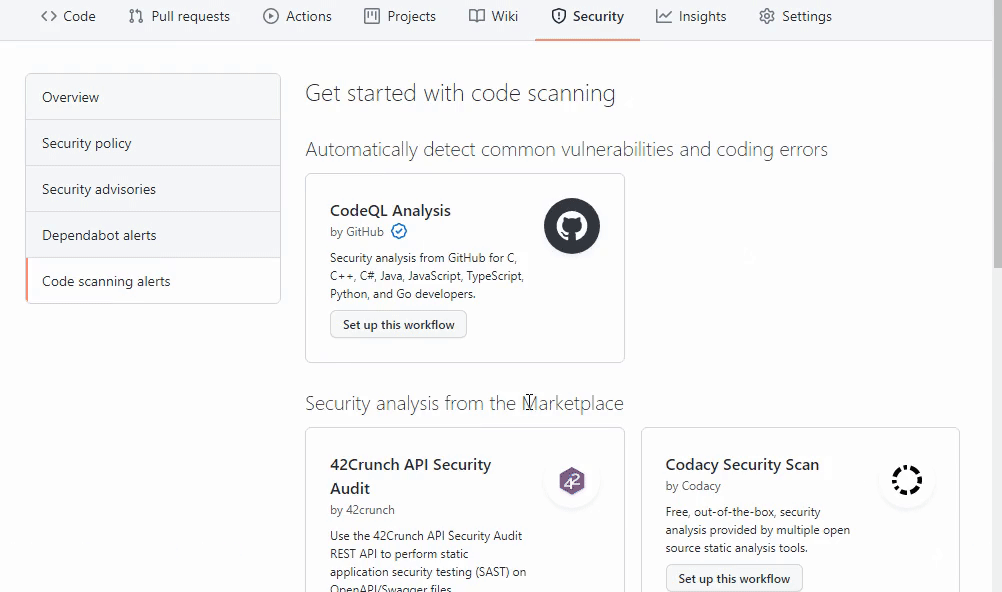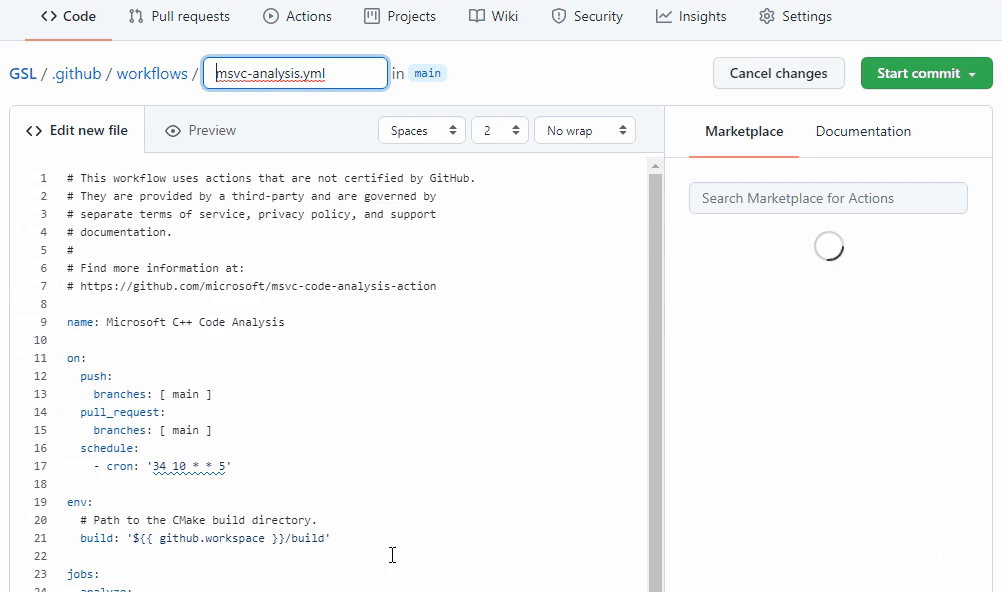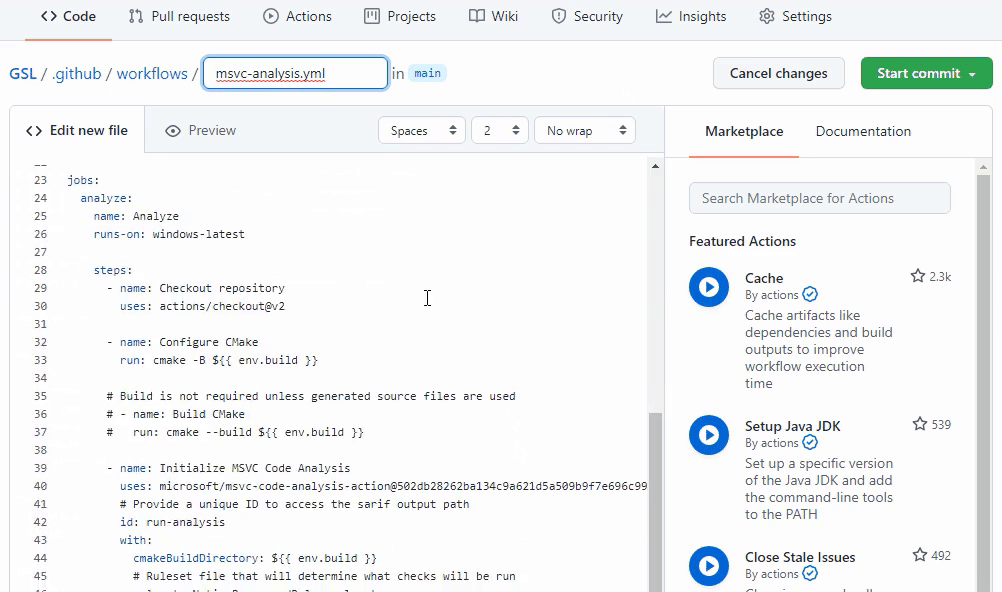
To get started using this experience you can find an entry for Microsoft C++ Code Analysis on the Security (tab) -> Setup up code scanning page if C++ is detected in your repository.
Once you have the template installed you can customize it to adapt to the specific needs of your repository. You can configure options such as ignoring a set of targets used for testing or changing the Ruleset file. The Ruleset file allows you to customize which warnings will be run beyond the default behavior. You can select a predefined ruleset available in a Visual Studio install (inside the ‘Team ToolsStatic Analysis ToolsRule Sets’ directory) or reference a customized file checked-in to the source. For the best results create a custom ruleset that adds/removes warnings from official rulesets in VS. This will ensure you receive updated checks as more are developed. Refer to the documentation on rulesets for more information.
Example Ruleset
<?xml version="1.0" encoding="utf-8"?>
<RuleSet Name="Example" Description="Enable Warnings" ToolsVersion="10.0">
<!-- Default rules available in Visual Studio -->
<Include Path="NativeRecommendedRules.ruleset" Action="Default" />
<Rules AnalyzerId="Microsoft.Analyzers.NativeCodeAnalysis"
RuleNamespace="Microsoft.Rules.Native">
<Rule Id="C26440" Action="None" /> <!-- Exclude: Declare noexcept -->
<Rule Id="C26492" Action="None" /> <!-- Include: No const_cast<> -->
</Rules>
</RuleSet> Feedback
The action is published under a pre-release status as it is tested on additional GitHub repositories and more features are added. We would love to hear feedback from you on how we can improve the Action to make it compatible with your GitHub projects. If you have a need for Native MSBuild support, please express your interest on the following feature request ticket.

You didn’t add a summary for front page. Currently, front page says:
Microsoft C++ Code Analysis with GitHub Actions
Daniel Winsor October 26, 2021
Summary of your post, shown on the home page next to the featured image
Pity this cannot be used for Windows developers, so we get stuck using the analyzers from the Visual Studio or making use of our investments into SonarQube instead.
For some workflows there is only MSBuild support like Win32, MFC and WinUI/UWP, for others like in this case, we only get CMake support.
Previous feature request tickets don’t tend to have good success rate anyway.
Hi Paulo, if you have a need for native MSBuild support, please express your interest on the following feature request ticket. The work that we do is heavily influenced by your feedback and helps us prioritize feature backlogs.