The public preview of role-based access control (RBAC) for the Azure Cosmos DB Core (SQL) API was announced today at Microsoft Ignite. With RBAC in Azure Cosmos DB, you can now:
- Authenticate your data requests with an Azure Active Directory (AD) identity.
- Authorize your data requests with a fine-grained, role-based permission model.
- Audit your diagnostic logs to retrieve the Azure AD identity used when accessing your data.
What is RBAC?
The concepts exposed by the Azure Cosmos DB RBAC should look very familiar to anyone who has used Azure RBAC before.
- Our new permission model exposes a set of actions that map to database operations (like writing a document or executing a query).
- You can create role definitions by assembling a list of actions that a role should allow.
- You associate your role definitions with Azure AD identities through role assignments. Roles can be assigned at the Azure Cosmos DB account, database or container levels.
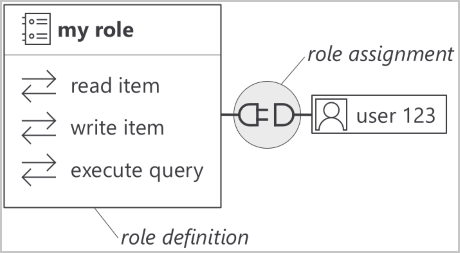
The granularity of the permission model lets you control very precisely what a client is allowed to do. Some examples of custom role definitions:
- A read-only role that can only fetch documents by their ID, but not run queries or read from the change feed.
- A role that can only insert new documents to an Azure Cosmos DB container, but not read, replace or delete documents.
Find the complete list of available actions.
Managing your role
No more primary keys!
TokenCredential instance that will resolve to the desired identity:Advanced auditing of data requests
- The Azure AD identity used to authenticate the request.
- The ID of the role assignment used to authorize the request.
AzureDiagnostics
| where ResourceProvider == "MICROSOFT.DOCUMENTDB"
and Category == "DataPlaneRequests"
and ResourceId == "<yourAccountResourceId>"
and OperationName == 'Query'
| summarize by aadPrincipalId_g, aadAppliedRoleAssignmentId_g
Getting started
You can start using role-based access control today to tighten the access control to your Azure Cosmos DB resources. Just head to the detailed documentation of the Azure Cosmos DB RBAC to get started!
New to Azure Cosmos DB?
- Try Azure Cosmos DB free in production or non-production environments
- Download the free best practices and optimization guide
- Visit MS Learn to build your Azure Cosmos DB skills

Hey,
Is this being fuly suppored in Azure Global, Azure Government & Azure China 21Vianet?
Why this is not being mentioned here – https://docs.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/services-support-managed-identities#azure-service-bus
Thanks,
Guy
Hi Guy,
As we’re still in preview, this feature is only available in the public Azure clouds. Support for sovereign clouds will come once it becomes generally available.
The link you’ve pasted is for Managed Identities support, which is a different feature.
And just where exactly was this feature on this list…
https://feedback.azure.com/forums/263030-azure-cosmos-db
You guys ignore features that people have been asking for FOR YEARS.
Are you guys strapped for cash?
Do you just not give a **ck?
Have the decency to either get rid of the feature request page or actually start working on the features that your developers are asking for.
Hi Jack, our new role-based access control with Azure AD addresses this customer request in particular: https://feedback.azure.com/forums/263030-azure-cosmos-db/suggestions/18607447-integrate-with-azure-active-directory.
Hope this helps!