Azure Cosmos DB Data Explorer is a web-based tool that allows you to interact with your data, run queries, and visualize results in Azure Cosmos DB. It is available in the Azure Portal and as a standalone web app.
RBAC allows you to use Microsoft Entra ID identities to control data access in Data Explorer, instead of using account keys. This way, you can grant granular permissions to different users and groups and audit their activities. RBAC also enables you to use features such as Entra ID Conditional Access and Entra ID Privileged Identity Management to further protect your data. It allows for finer-grained access control based on roles, reducing the risk associated with key management and distribution.
Previously, RBAC could only be used with the standalone app, and not directly within the Data Explorer in the Azure portal. Today you have enhanced capabilities, and you can use it within the Data Explorer in the portal and the standalone Data Explorer web app for your Azure Cosmos DB NoSQL accounts.
How to enable RBAC in Data Explorer for NoSQL accounts
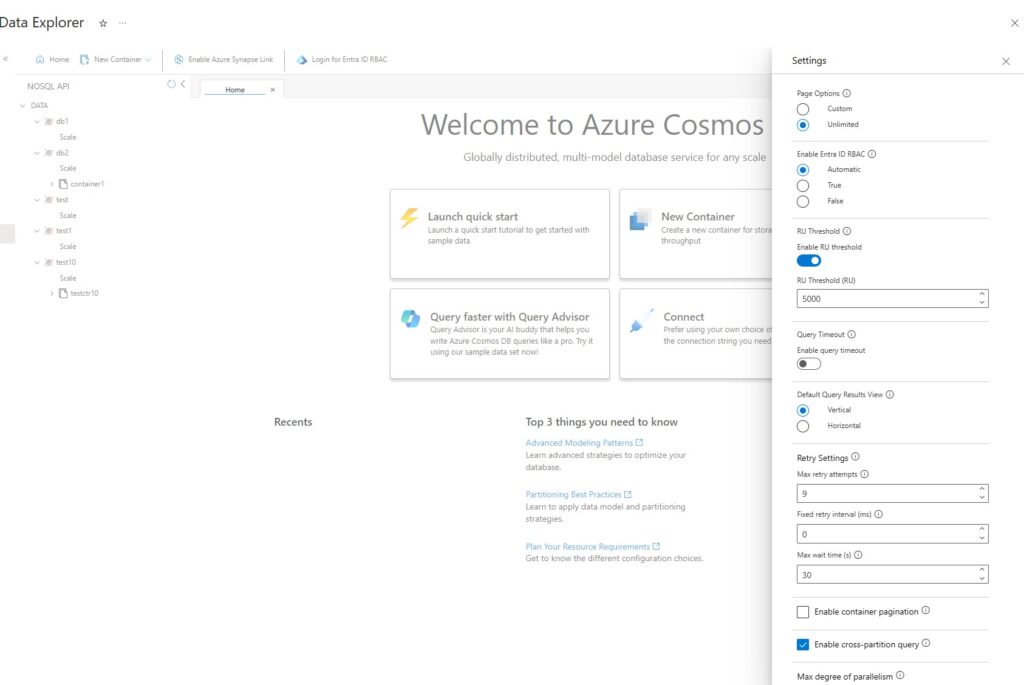
The use of RBAC in Data Explorer is controlled by the Enable Entra ID RBAC setting. You can access this setting via the “wheel” icon at the upper right-hand side of Data Explorer.
The setting has three values tailored to your needs:
- Automatic (default): In this mode, RBAC will be automatically used if the account has disabled the use of keys. Otherwise, Data Explorer will use account keys for requests.
- True: In this mode, RBAC will always be used for Data Explorer requests. If the account has not been enabled for RBAC, then the requests will fail.
- False: In this mode, account keys will always be used for Data Explorer requests. If the account has disabled the use of keys, then the requests will fail.
Previously, RBAC was only supported in the Data Explorer standalone web app using a feature enabled link. This is still supported and will override the value of the Enable Entra ID RBAC setting. Using this query parameter is equivalent to using the ‘Automatic’ mode mentioned above.
How to use RBAC in Data Explorer
Once you have enabled RBAC and assigned roles to your Entra ID identities, you can use Data Explorer to interact with your data. To do so, you need to sign in to Data Explorer with your Entra ID credentials, either in the Azure Portal or in the standalone web app. You will see a list of Azure Cosmos DB accounts that you have access to, and you can select the one you want to work with. Depending on the role you have been assigned, you can perform different actions in Data Explorer.
Conclusion
RBAC is a powerful feature that enhances the security and governance of your Azure Cosmos Db accounts, by allowing you to use Entra ID identities to control data access. RBAC also enables you to leverage other Entra ID features, such as Conditional Access and Privileged Identity Management, to further protect your data. RBAC is easy to enable and use, and it provides granular and auditable permissions for different users and groups.
Try it out and please share your feedback through the feedback icon in Data Explorer.
Learn more: Configure role-based access control with Microsoft Entra ID – Azure Cosmos Db | Microsoft Learn
About Azure Cosmos DB
Azure Cosmos DB is a fully managed and serverless distributed database for modern app development, with SLA-backed speed and availability, automatic and instant scalability, and support for open-source PostgreSQL, MongoDB, and Apache Cassandra. Try Azure Cosmos DB for free here. To stay in the loop on Azure Cosmos DB updates, follow us on X, YouTube, and LinkedIn.


Is this GA?
The options for Enable Entra ID are missing from the blade.
Explorer Version
17754cba05e4d1a156b536dad388f17d83a0ff9b
Same for me.
Hi Thomas and Jonathon, I trust the issue is resolved? The feature is GA.