Built-in security for every configuration
Azure Cosmos DB for MongoDB vCore is designed with security as a foundational principle. Regardless of how your cluster is configured—whether it’s a single-node deployment or a multi-shard architecture—your data is always encrypted at rest using the AES-256 cipher, one of the most trusted and widely adopted encryption standards.
This encryption is automatically handled using a service-managed key (SMK). There’s no setup required, no toggle to enable—it’s always on. SMK-based encryption ensures that your data is protected by default, delivering all the benefits of AES-256 encryption, including compliance with industry standards such as ISO/IEC 27001, HIPAA, and GDPR.
Note: Customer-managed key (CMK) is now generally available (GA) in Azure Cosmos DB for MongoDB vCore.
Introducing customer-managed key (CMK) support
For organizations that require greater control over their encryption strategy, Azure Cosmos DB for MongoDB vCore now supports customer-managed keys (CMK). This feature allows customers to own and manage the encryption keys used to protect their data—adding a layer of control and flexibility on top of the default SMK.
Here’s how it works:
- CMK is used to encrypt the SMK, which in turn encrypts the data at rest.
- This means customers retain full control over access to their data.
- If a customer revokes the CMK, the SMK becomes inaccessible, and the data in the cluster is rendered unreadable.
This capability is especially valuable for organizations with strict compliance requirements, internal security policies, or a need to enforce key lifecycle management.
Where CMK is supported
CMK encryption is available across multiple cluster types:
- Primary (read-write) clusters
- Replica clusters
- Restored clusters
You can choose to enable CMK on all your Azure Cosmos DB for MongoDB vCore clusters or selectively apply it to specific clusters based on your security needs. This flexibility allows you to tailor your encryption strategy to different environments, use cases, or compliance zones.
Versionless key model for seamless rotation
Azure Cosmos DB for MongoDB vCore uses a versionless key model for CMK. This means:
- The cluster always uses the latest version of the specified key stored in Azure Key Vault.
- You don’t need to manually update the key reference in the cluster configuration.
- Simply configure key auto-rotation in Azure Key Vault, and the cluster will automatically use the most recent version.
This approach simplifies key management while ensuring that your encryption strategy remains up to date and aligned with best practices. It also reduces operational overhead and minimizes the risk of misconfiguration during key updates.
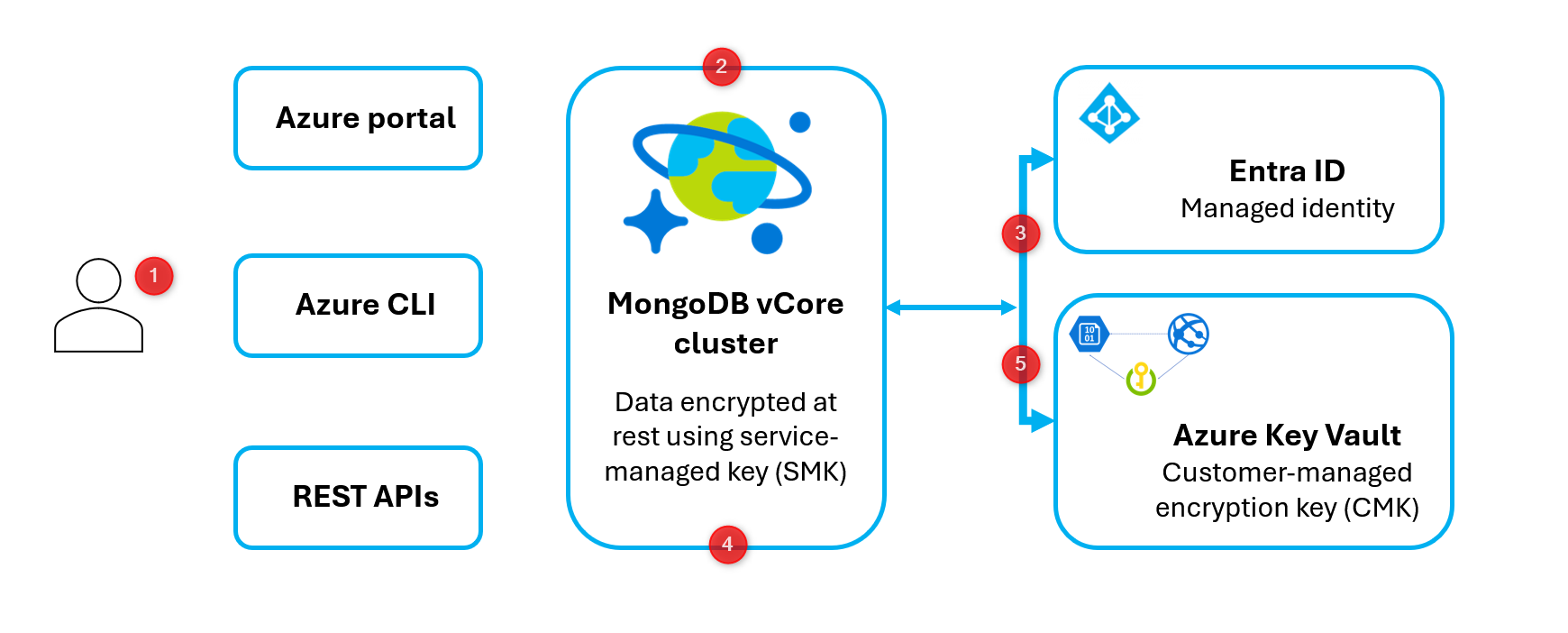
How customer-managed key (CMK) works
Azure Cosmos DB for MongoDB vCore uses Azure Key Vault to store the customer-managed key (CMK), which is used to encrypt the service-managed key (SMK). The SMK, in turn, encrypts the data within the cluster. A managed identity in Microsoft Entra ID is used to access the customer’s encryption key stored in Azure Key Vault.
The following diagram illustrates how these components interact to provide you full control over data encryption in Azure Cosmos DB for MongoDB vCore.
Figure 1. Customer-managed key (CMK) flow in Azure Cosmos DB for MongoDB vCore.
The following list explains the numbered steps in the diagram:
- An Azure Key Vault admin grants permissions to encryption keys stored in key vault to a managed identity in Microsoft Entra ID.
- An Azure Cosmos DB for MongoDB vCore administrator configures encryption with a customer-managed key (CMK) for the cluster.
- Azure Cosmos DB for MongoDB vCore uses the managed identity configured in step 1 to authenticate to Azure Key Vault via Microsoft Entra ID.
- Azure Cosmos DB for MongoDB vCore wraps the cluster storage encryption key with the customer-managed key in Azure Key Vault.
- For read/write operations, Azure Cosmos DB for MongoDB vCore sends requests to Azure Key Vault to unwrap the cluster data encryption key to perform encryption and decryption operations.
How to set up data encryption with customer-managed key on an Azure Cosmos DB for MongoDB vCore cluster
You can enable CMK during new cluster provisioning, replica cluster creation, or when requesting a cluster restore. Once a CMK-enabled cluster is created, you can configure CMK settings such as the user-assigned managed identity and the encryption key to be used.
To set up CMK on an Azure Cosmos DB for MongoDB vCore cluster, you’ll need the following:
- A user-assigned managed identity
- An Azure Key Vault with specific configuration settings
- An asymmetric or RSA encryption key in enabled state within the Azure Key Vault. You can import an existing encryption key and use it for your cluster’s data encryption.
- Permissions granted to the user-assigned managed identity to access the Azure Key Vault where the encryption key is stored
It’s important that the cluster, user-assigned managed identity, and Azure Key Vault are located in the same Azure region and within the same Microsoft Entra tenant.
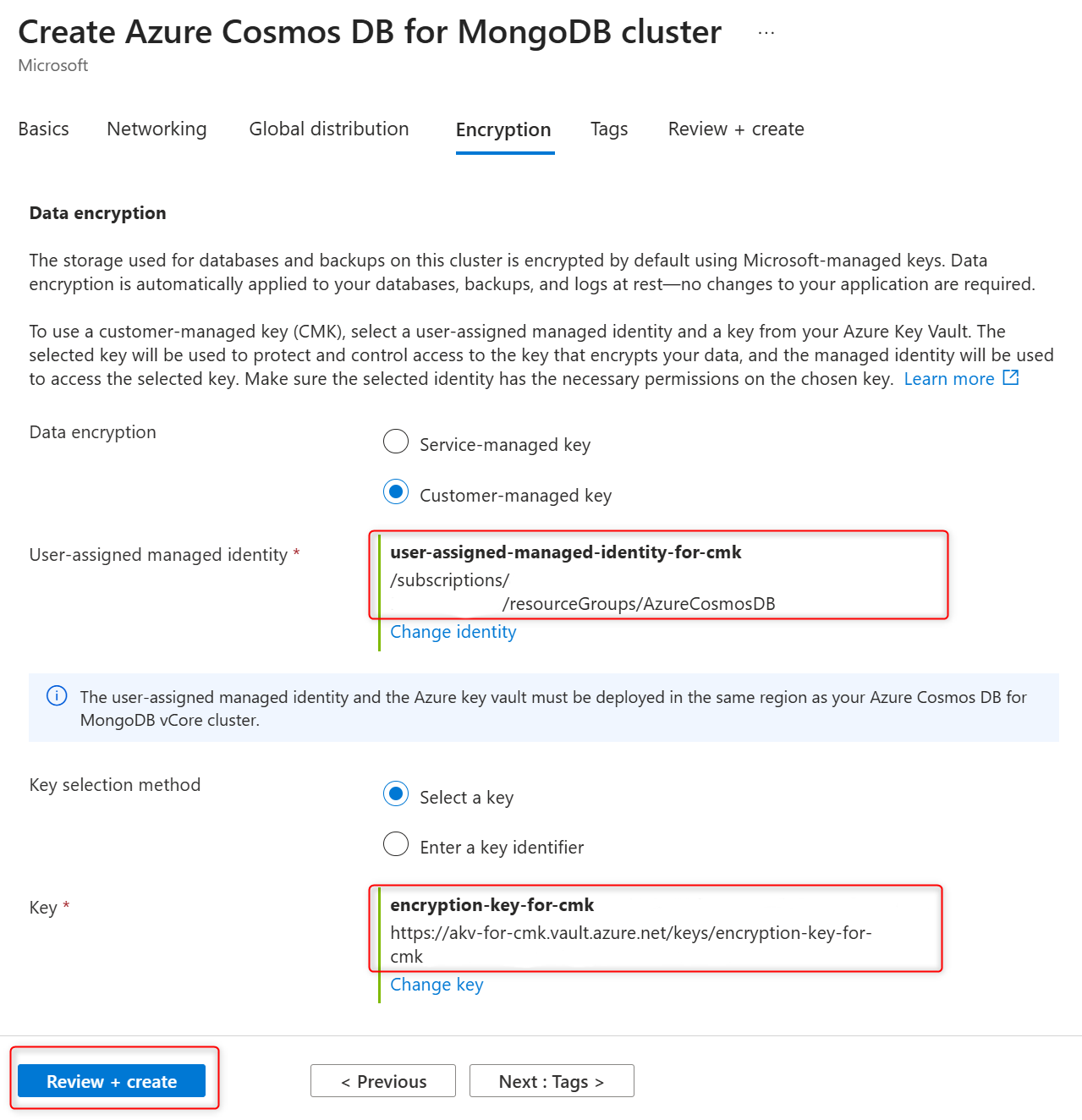
Once all components are in place, you’re ready to configure CMK during cluster provisioning. Follow these steps:
- Fill in the required information on the Basics tab.
- Navigate to the Encryption tab.
- Select Customer-managed key.
- Specify the user-assigned managed identity to access the encryption key.
- Select the Azure Key Vault and the encryption key to be used.
 Figure 2. CMK configuration during cluster provisioning in Azure portal.
Figure 2. CMK configuration during cluster provisioning in Azure portal. - Go to the Review + create tab and click Create.
After the cluster is created, open its properties and verify on the Overview page that data encryption with customer-managed key is enabled.
You can use Azure portal, Azure CLI, Azure SDKs, or REST APIs to perform all management operations for CMK in Azure Cosmos DB for MongoDB vCore.
Next steps
To learn more and get started with CMK in Azure Cosmos DB for MongoDB vCore, explore the official documentation:
- Data encryption with customer-managed key (CMK) fundamentals
- How to manage data encryption with customer-managed key in Azure Cosmos for MongoDB vCore
About Azure Cosmos DB
Azure Cosmos DB is a fully managed and serverless distributed database for modern app development, with SLA-backed speed and availability, automatic and instant scalability, and support for open-source PostgreSQL, MongoDB, and Apache Cassandra. To stay in the loop on Azure Cosmos DB updates, follow us on X, YouTube, and LinkedIn.

0 comments