Zero Trust is a security architecture model that institutes a deny-until-verified approach for access to resources from both inside and outside the network. This approach addresses the challenges associated with a shifting security perimeter in a cloud-centric and mobile workforce era. The core principle of Zero Trust is maintaining strict access control. This concept is critical to prevent attackers from pivoting laterally and elevating access within an environment.
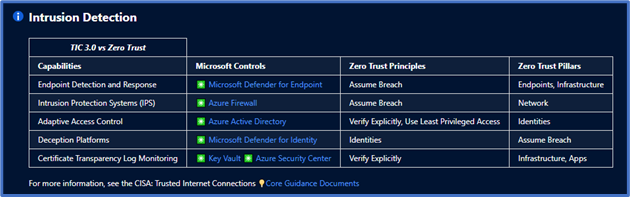
Microsoft has a capability to facilitate Zero Trust architectures in federal frameworks. The Azure Sentinel: Zero Trust (TIC 3.0) Workbook provides an overlay of Microsoft offerings to Zero Trust models, measurable over time via visualizations. Implementers, SecOps analysts, assessors, security and compliance decision makers, and managed security service providers (MSSPs) can leverage this capability to build, design, and monitor cloud security architectures. Each panel aligns to a specific control providing an actionable path to cover gaps, build alerting, and even incorporate third-party security investments.
At Microsoft, we define Zero Trust around universal principles.
- Verify explicitly: Always authenticate and authorize based on all available data points, including user identity, location, device health, service or workload, data classification, and anomalies.
- Use least-privileged access: Limit user access with just-in-time and just-enough-access (JIT/JEA), risk-based adaptive policies, and data protection to secure both data and productivity.
- Assume breach: Minimize blast radius for breaches and prevent lateral movement by segmenting access by the network, user, devices, and app awareness. Verify all sessions are encrypted end-to-end. Use analytics to get visibility, drive threat detection, and improve defenses.
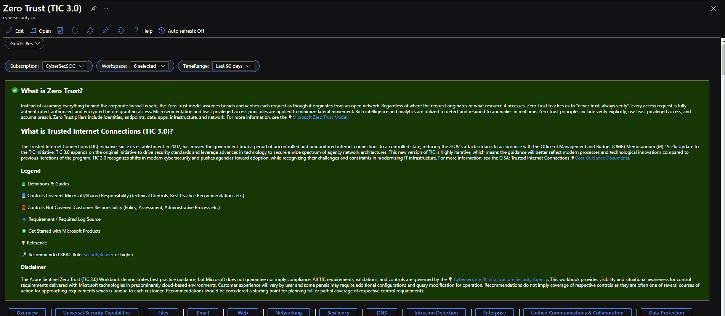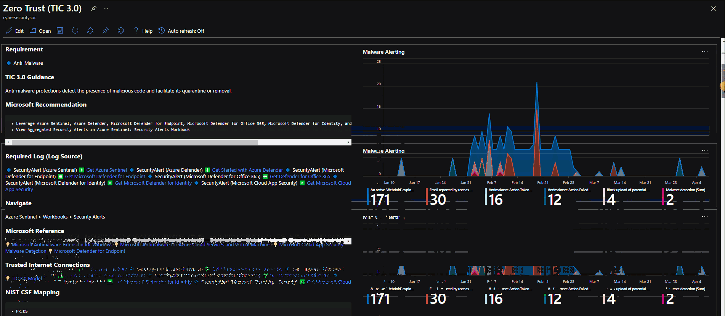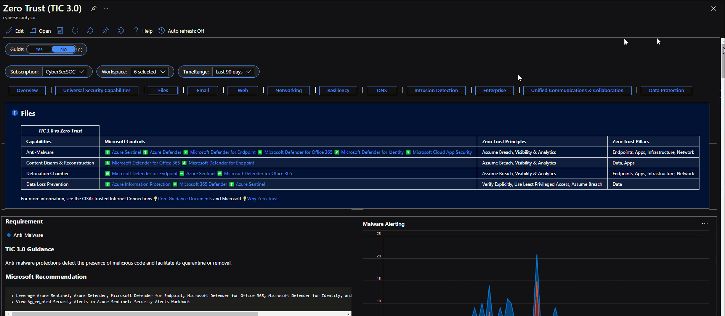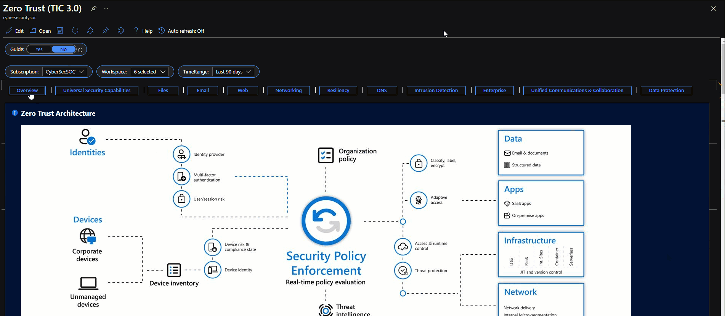
These principles are technology-agnostic and aligned to six Zero Trust pillars.
- Identity: Whether they represent people, services, or IoT devices—define the Zero Trust control plane. When an identity attempts to access a resource, verify that identity with strong authentication, and ensure access is compliant and typical.
- Endpoints: Once an identity accesses a resource, data can flow to different endpoints—from IoT devices to smartphones, BYOD to partner-managed devices, and on-premises workloads to cloud-hosted servers. This diversity creates a massive attack surface area. Monitor and enforce device health and compliance for secure access.
- Data: Ultimately, security teams are protecting data. Where possible, data should remain safe even if it leaves the devices, apps, infrastructure, and networks the organization controls. Classify, label, and encrypt data, and restrict access based on those attributes.
- Apps: Applications and APIs provide an interface for data consumption. They may be legacy on-premises, lifted-and-shifted to cloud workloads, or modern SaaS applications. Apply controls and technologies to discover shadow IT, ensure appropriate in-app permissions, gate access based on real-time analytics, monitor for abnormal behavior, control user actions, and validate secure configuration options.
- Infrastructure: Infrastructure—whether on-premises servers, cloud-based VMs, containers, or micro-services—represents a critical threat vector. Assess for version, configuration, and JIT access to harden defense. Use telemetry to detect attacks and anomalies, and automatically block and flag risky behavior and take protective actions.
- Network: All data transits over network infrastructure. Networking controls can provide critical controls to enhance visibility and prevent attackers from moving laterally across the network. Segment networks and deploy real-time threat protection, end-to-end encryption, monitoring, and analytics.
Defining Zero Trust with government frameworks
Governance definition is a critical precursor to any Zero Trust initiative. For federal agencies, this means evaluating the available federal frameworks. There are several references for implementing Zero Trust in federal information systems, including NIST SP 800-207, TIC 3.0, and CDM:
- The National Institute of Standards and Technology (NIST) has recently released NIST SP 800-207. This document provides a framework for designing a zero-trust architecture (ZTA) network strategy.
- Trusted Internet Connections (TIC) is a federal cybersecurity initiative to enhance network and perimeter security across the US federal government. The TIC initiative is a collaborative effort between the Office of Management and Budget (OMB), the Department of Homeland Security (DHS), Cybersecurity and Infrastructure Security Agency (CISA), and the General Services Administration (GSA). The TIC 3.0: Volume 3 Security Capabilities Handbook provides various security controls, applications, and best practices for risk management in federal information systems.
- Continuous Diagnostics and Mitigation (CDM) is a program led by the Cybersecurity and Infrastructure Security Agency (CISA). The CDM program delivers cybersecurity capabilities across the federal government, including providing cybersecurity tools, services, reporting, and best practices. The Continuous Diagnostics and Mitigation Program Fact Sheet outlines five key program areas: dashboarding, asset management, identity and access management, network security management, and data protection management.
This workbook leverages automation to visualize your Zero Trust security architecture. It provides detailed crosswalks of Microsoft’s Zero Trust model with the TIC 3.0 framework.
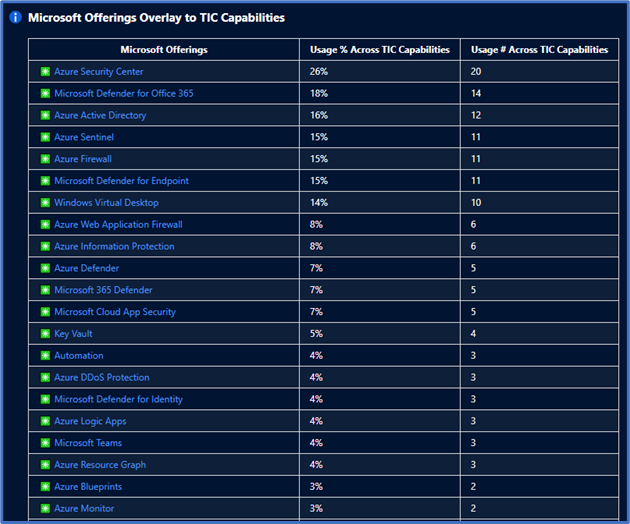
There’s also a detailed mapping of each Microsoft offering to individual requirements. This offering helps plan security architectures and evaluate the capabilities of respective Microsoft Security tooling.
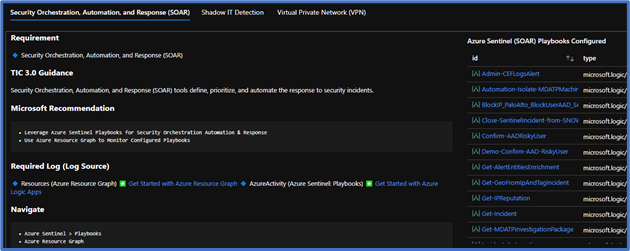
Each control panel provides an actionable visualization of your security controls with tailored recommendations to cover gaps. TIC 3.0 provides mapping to NIST principles which help apply these principles across similar government compliance frameworks.
This workbook augments staffing and keeps your security teams doing what they do best. Each recommendation is grounded in Microsoft documentation, industry references, and best practice. You’ll also have a starting point in exploring your security architecture with dozens of queries you can leverage for alerting and monitoring. Workbooks is a flexible platform, and you can readily customize each panel to incorporate your organization’s unique requirements.
Deploying the workbook
It is recommended that you have the log sources listed above to get the full benefit of the Zero Trust (TIC 3.0) Workbook, but the workbook will deploy regardless of your available log sources. Follow the steps below to enable the workbook:
Requirements: Azure Sentinel Workspace and Security Reader rights.
1) From Azure Portal, or Azure GOV Portal navigate to Azure Sentinel
2) Select Workbooks > Templates
3) Search Zero Trust and select Save to add to My Workbooks
Watch the Azure Sentinel: Zero Trust (TIC 3.0) Workbook demo
For more information on the Azure Sentinel: Zero Trust (TIC 3.0) Workbook, see Announcing the Azure Sentinel: Zero Trust (TIC3.0) Workbook
To learn more about Zero Trust with Microsoft, see Enabling a remote workforce by embracing Zero Trust security

Nice article, but the title needs to change. It effectively reads ‘government has zero trust in Azure’… !