Securing the endpoint: designing SaaS service implementations to meet federal policy (2 of 4)
Several federal initiatives such as CDM (Continuous Diagnostic and Mitigation), TIC (Trusted Internet Connection) increasingly becoming similar, in that identical tools and approaches such as Zero Trust can be used to meet multiple federal mandates. This convergence provides an opportunity to reduce complexity while helping agencies improve their security posture and increase IT efficiency.
This blog, the second of a four-part series on meeting federal mandates with SaaS services, provides a deep dive on securing endpoints regardless of their location. The first blog focused on securing mobile.
Adopting a Zero Trust architecture with endpoint protection
Zero Trust eliminates the concept of trust based on network location within a perimeter. Instead, the architecture leverages device and user verification to gate access to organizational data and resources. Gaining visibility to a user and their device becomes critical when access is allowed from any location and corporate data no longer resides behind the organizations firewall.
What if the endpoint continuously fed the corporate security tools events and data, regardless of location, and allowed IT to control data movement? MDTAP is an Endpoint Detection and Response/Endpoint Protection Platform (EDR/EPP) solution that provides visibility and control of an endpoint regardless of the device location.
What makes MDATP unique is the signal sharing between other Microsoft security solutions. With a simple slide of a switch, MDATP is sharing signals from the endpoint and enriching other security services like Microsoft’s Intune, Office 365 Threat Intelligence, Azure Information Protection (AIP), Microsoft Cloud App Security (MCAS) and more.
Using Intune to manage Defender policies and achieve a shared signal
In the Securing Mobile post of this series, we talked about how Azure Active Directory conditional access policies (CAPs) can be used to control access to data and require devices to be managed before accessing organizational resources.
When a device is enrolled into Microsoft Intune there are built in- polices that configure the enrollment into MDATP. The device becomes fully managed from Intune, receiving security and compliance polices. Intune also configures the Defender policies for the operating system as part of this enrollment.
This simplifies the tasks that IT organizations must perform to bring a device into compliance and start receiving critical threat data. If you recall from the previous section, MDATP is also feeding several other Microsoft security solutions. The simple task of enrolling a device into Microsoft Intune reveals the power of signal sharing between Microsoft solutions.
Microsoft is continuously adding security features into Windows 10 to meet modern threats. Organizations generally understand the importance of updating to a modern operating system to take advantage of the newest security controls. This becomes even more important to the organization’s digital estate with modern cybersecurity architectures because device attestation is critical to Zero Trust. Configuring Defender controls like Device Guard, Application Guard, Exploit Guard and using the AMSI Interface for antimalware are essential to securing the endpoint. Those controls also provide device health information that can be used in Conditional Access Policies, working in conjunction with MDATP.
Assessing vulnerabilities continuously with MDATP
Every day we hear of organizations responding to cyber incidents. Many of the breaches occur from unpatched systems, even though a patch was released months before the breach. The list of vulnerabilities seems to grow daily, and IT staff struggles to keep up. Many organizations run vulnerability scans at various intervals, but their data is only as good as the last scan.
MDATP can perform a vulnerability assessment on endpoints displaying operating system or applications weaknesses. MDATP doesn’t rely on a scan — the service continuously checks the system for vulnerabilities in near real time, keeping the organization informed about the newest threats. Microsoft includes the Threat & Vulnerability Management (TVM) dashboard in MDATP. TVM provides an organization an Exposure score and highlights top security recommendations across the entire organization into a single view.
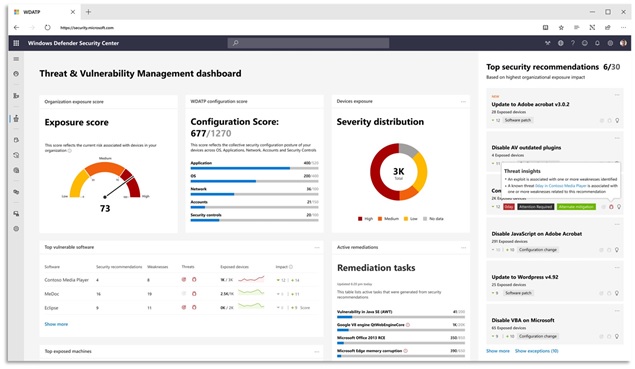
Figure 1 MDATP Threat & Vulnerability Management Dashboard
Advanced threat hunting to monitor endpoints
In addition to dashboards, security teams often want the ability to automate monitoring and investigate entities that span multiple indicators. MDATP provides security teams deeper access to the data in threat hunting tables. The hunting tables include TVM data, letting your security teams hunt for known software vulnerabilities, process creation events, and much more. Advanced hunting is critical to monitoring an endpoint to identify potential compromises in an organization.
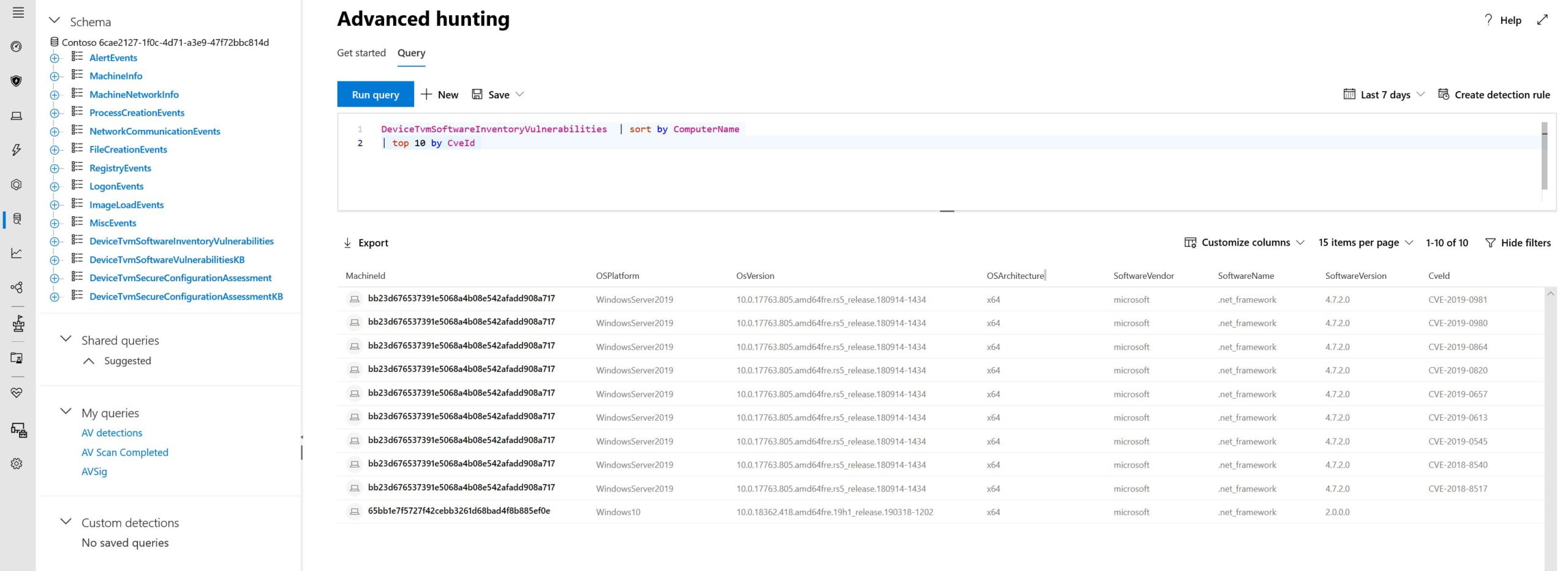
Figure 2 MDATP Advanced Hunting Tables
Remediating vulnerabilities across teams
Finding security vulnerabilities on your network is challenging enough. Remediating those vulnerabilities typically moves across teams in organizations. Security teams are forced to send emails to track status, use multiple tools to discover and remediate issues, all the while leaving organizations vulnerable to attack.
MDATP provides native integration with tools like ServiceNow and Microsoft’s Intune allowing security teams to start a remediation task from MDATP. The remediation view provides the security team visibility into the status of the remediation task, including who initiated it and when it’s due. If you’re using Microsoft Intune, this task will be sent over as a security task with all the required information to deploy a fix to the affected endpoints.
Isolating endpoints to protect organizations from malware
To protect organizations from malware, you many need to isolate resources from the network. Since MDATP is a cloud service, anytime a device has connectivity it’s managed by the service. This allows organizations to isolate endpoints regardless of location. IT staff will be prompted to allow services like email to continue or be blocked before the machine is isolated. Isolation will block all traffic to and from the endpoint except for the MDATP service.
When a machine is isolated, security teams still have control of the endpoint via the MDATP service. Live Response provides the ability to investigate endpoints regardless of its physical location. Security staff can upload/download programs to perform security tasks or create a script library that can be used to investigate the endpoint. This is extremely powerful to an organization, providing complete visibility and control of a device anywhere in the world.
Blocking endpoints from communicating with known threats
As organization discover new threats, there is a need to block endpoints from communicating with known Indicators of Compromise (IOC). MDATP allows security teams to create indicators to block additional items like IPs/URLs and File hashes. When organizations discover threats like a Zero-day attack and quickly need to block all endpoints from communicating to known malicious IPs, organizations can create a custom rule(s) to easily achieve this. After IT creates an indicator, any machine attempting to communicate with the IP/URL will generate an alert, block the communication and, optionally, initiate an automatic investigation of the endpoint.
Most organizations bounce from tool to tool attempting to discover where the initial compromise had occurred. One reason this happens is the lack of signal sharing between tools. Signal sharing between Microsoft services such as MDATP provides security teams a view of the entire structure of an attack and starts investigating the endpoint immediately. The automatic investigation helps expedite the security team’s tasks by pulling logs and key data points from the endpoint and correlating those events.
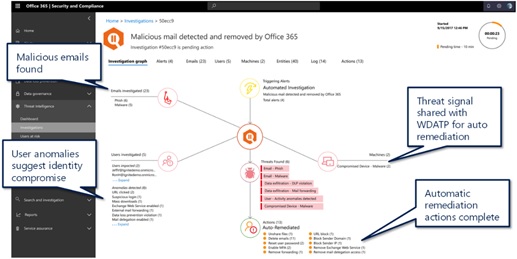
Figure 3 Office 365 Threat Management investigations
Identifying sensitive data on endpoints with Azure Information Protection (AIP)
We live in a data driven world and protecting organizational information and preventing leaks and spills is extremely important. MDATP and Azure Information Protection (AIP) work together to identify sensitive data on endpoints. The MDATP service communicates with AIP to provide organizations a dashboard of all their sensitive data and who is access it.
It’s important to note that all devices are not equal; this is because some devices contain sensitive information while others do not. MDATP provides a device risk level, the risk level factors include various elements such as hosting sensitive data. Since Microsoft solutions have a shared signal, if a device is known to host sensitive information, the risk factor is increased on the endpoint. When multiple alerts arrive, security teams can prioritize devices with the highest risk, allowing organizations to focus their efforts on the proper devices first.
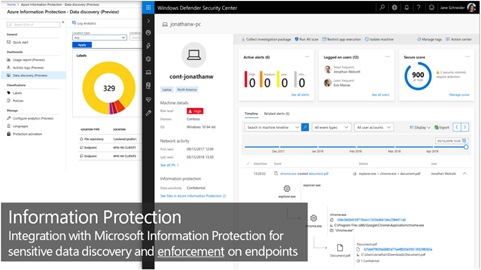
Figure 4 Azure AIP Dashboard and MDATP machine page
Managing data across cloud apps
When talking about Data Loss Prevention (DLP) or data leakage, we know users move data, and quite often organizational data moves to cloud services like Box, Google Drive, and other SaaS platforms that aren’t visible to the organization’s IT team.
In the “Securing Mobile” article we talked about how AIP polices move with the document, but what if documents haven’t been labeled and sit outside the corporate boundary? MDATP integrates natively with Microsoft Cloud App Security (MCAS) to provide additional policy control for data movement. The MDATP service monitors all activity on a managed endpoint and the MDATP service will pass information to MCAS.
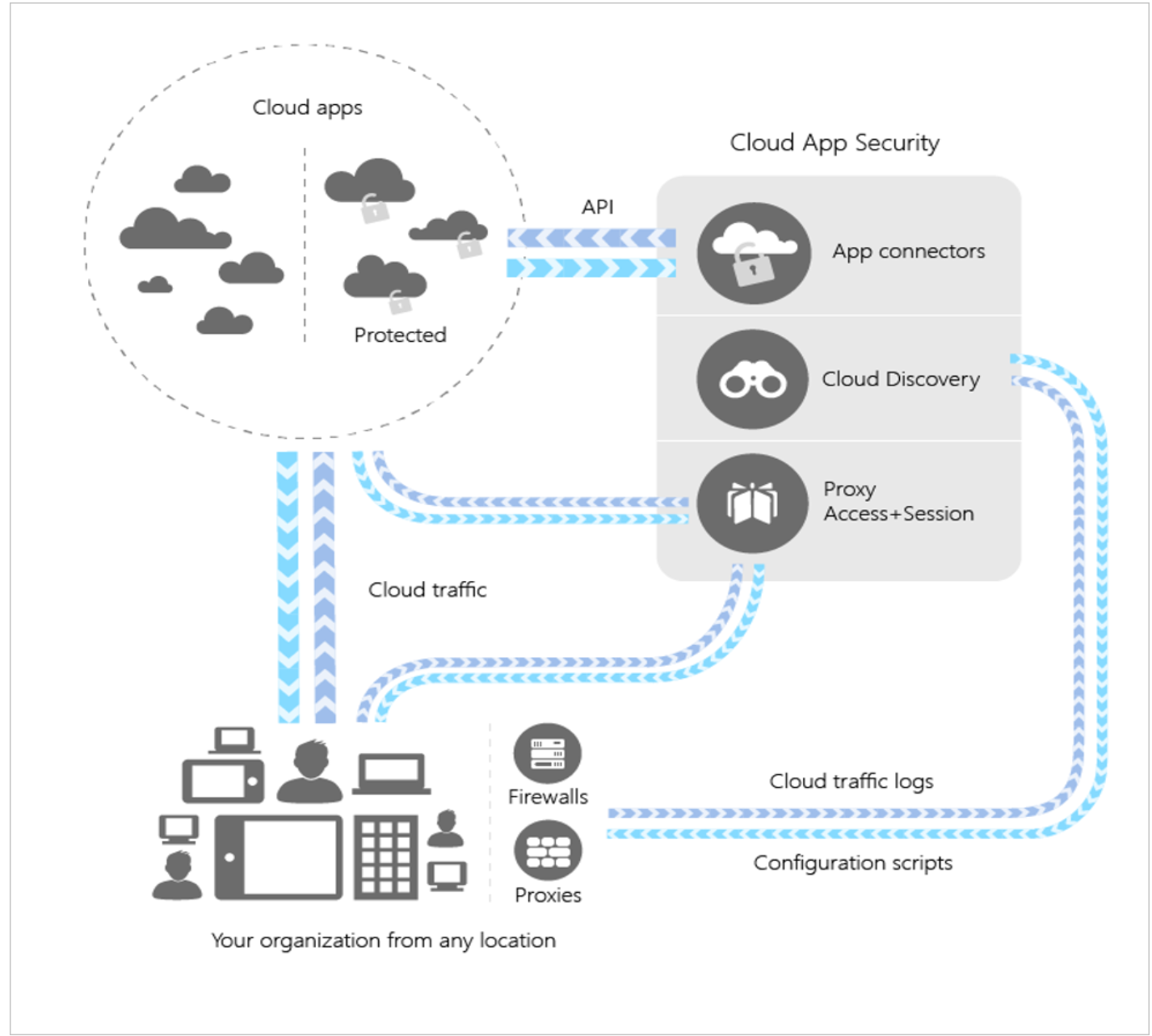
Figure 5 MCAS overview
While monitoring the endpoint, the integration between MDATP and MCAS helps organizations discover cloud apps being used and who is using them. The Cloud Discovery dashboard is designed to give you more insight into how over 16,000 cloud apps are being used in your organization. It provides an at-a-glance overview of what kinds of apps are being used, your open alerts, and the risk levels of apps in your organization. The dashboard is populated by ingesting firewall logs or directly from clients enrolled in MDATP. This means anywhere in the world your devices go, the endpoints will feed the MCAS service allowing organizations visibility into usage and the ability to create polices to protect data.
Implementing cloud data controls with MCAS
MCAS provides organizations the ability to create policies that define how users behave in the cloud. MCAS Policies enable organizations to detect risky behavior, violations, or suspicious data points and activities in your cloud environment; all based on user, location, device, and app. MCAS provides native connectors to several 3rd party cloud solutions, allowing organizations to implement data controls from a single location across numerous solutions.
For example, a policy can discover Personally Identifying Information (PII) data stored in a document in OneDrive and allow organizations to take specific action if a document matches a policy. MCAS can automatically apply AIP labels protecting the document, notify a manager, and various other controls. This helps security teams understand where data resides and who has access to the data.
Identifying risk is critical for an organization, especially when it comes to user’s activity. Microsoft believes identity is the new security perimeter and understanding user activity is imperative. Azure Advanced Threat Protection (ATP) is a cloud-based security solution that leverages your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization. Azure ATP, Microsoft Cloud App Security (MCAS), and Azure AD Identity Protection add powerful User and Entity Behavior Analytics (UEBA) capabilities. Data is surfaced in MCAS to provide a single view for security teams into behavioral risk and works in conjunction with MCAS polices.
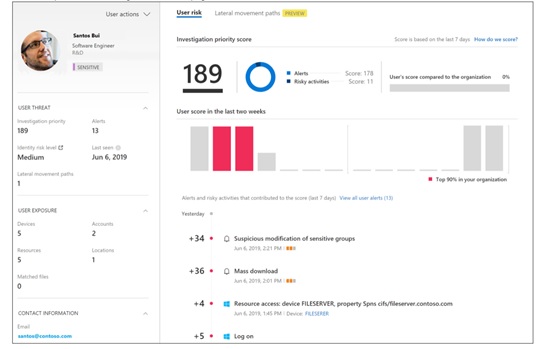
Figure 6 MCAS User Behavior Analysis
In this blog we discussed how solutions like Intune, MCAS, Azure AD, and MDATP can help secure endpoints and your data. Throughout this article we walked through some key concepts for an organization, however we only touched on the capabilities of the solutions outlined above. If you’re interested in learning more, visit the Microsoft Security site.

 Light
Light Dark
Dark
1 comment
Awesome Blog Brian Tirch – THANKS FOR THIS!!