Defending federal information systems with Azure Sentinel threat intelligence workbook
This blog is co-authored by TJ Banasik, CISSP-ISSEP, ISSAP, ISSMP, Senior Program Manager; and Lili Davoudian, Program Manager II of Microsoft Cloud & AI Security.
Threats against federal information systems are a rising concern requiring detailed understanding of threat actors, behavior, and methods. The Executive Order on Improving the Nation’s Cybersecurity details several requirements for removing barriers to sharing threat information, including access and insights into cyber threats and incident information. Threat intelligence is an advanced cybersecurity discipline requiring detailed knowledge of identifying and responding to an attacker based on observation of indicators in various stages of the attack cycle.
Azure Sentinel is a cloud-native SIEM (security information event management) solution that allows customers to import threat intelligence data from various places such as paid threat feeds, open-source feeds, and from various threat intelligence sharing communities. Azure Sentinel supports open-source standards to bring in feeds from threat intelligence platforms (TIPs) across STIX & TAXII. Microsoft has released the next evolution of threat hunting capabilities in the Azure Sentinel threat intelligence workbook.
Azure Sentinel threat intelligence is based on ingestion of threat indicators such as IP addresses, domains, URLs, email senders, and file hashes. This provides a starting point for building threat intelligence programs which require the ability to both ingest and correlate threat data across cloud workloads. Watch this demo for more details:
Benefits
- Ingest, analyze, hunt for indicators within workloads
- Free text search to hunt for IPs, hashes, emails, etc., across 50+ Microsoft telemetry components
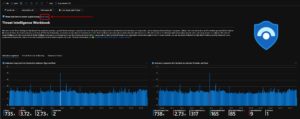
- Advanced correlations for artificial intelligence and machine learning (AI/ML), user entity behavior analytics (UEBA), and geospatial location of threats
- Find, fix, resolve workload weaknesses
- Query/alert generation
Getting started
The Azure Sentinel threat intelligence workbook provides the capability to both ingest and correlate threat data in cloud workloads. It also provides a free text search to hunt for IPs, hashes, emails etc., across 50+ Microsoft telemetry components. There are advanced correlations for AI/ML, UEBA, and geospatial location of threat sources. Here’s how to get started:
1. Onboard Azure Sentinel
2. Connect threat intelligence platforms
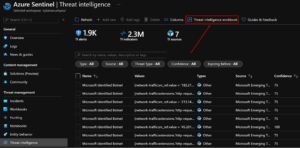
4. Access the content: Azure Sentinel > Threat intelligence > Threat intelligence workbook
5. Review the content and provide feedback through our survey
Learn more about threat intelligence with Microsoft Security
- General availability of Azure Sentinel Threat intelligence in Azure commercial and Azure Government
- Understand threat intelligence in Azure Sentinel
- Microsoft threat intelligence

 Light
Light Dark
Dark
0 comments