This guide demonstrates how to seamlessly set up user access in GitHub Enterprise using Security Assertion Markup Language (SAML) authentication. The process connects a user’s GitHub account with your organization’s identity provider (such as Microsoft Entra ID or Okta), enabling secure and streamlined access management.
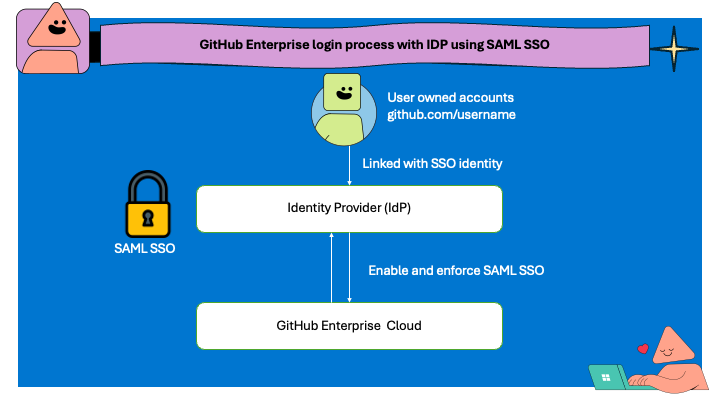
The diagram above describes the process when a user access GitHub Enterprise when SAML authentication, the critical piece here is the link with Single Sign-On (SSO) identity.
Assuming the following steps before starting:
- You have created your GitHub Enterprise
-
- This GitHub Enterprise is not an Enterprise Managed Users (EMU) instance
- You have created an Enterprise Application with your Identity Provider (IDP) and configured SAML. This establishes the security connection between GitHub and the IDP of choice. Here’s an example guide done with Microsoft Entra ID as the IDP: Tutorial: Microsoft Entra SSO integration with a GitHub Enterprise Cloud Organization
- You have assigned users access to the GitHub application in your IDP
Step by step Guide
Note: There will be up to 3 [personas] in this process.
Step 1 [as Owner of the GitHub Organization]: Invite the new user’s personal GitHub Account handle to the intended Organization within the GitHub Enterprise.

Step 2 [as ‘Cloud Application Administrator’ of Microsoft Entra ID Enterprise Application for GitHub Enterprise]: Add the account that you want linked to the new user’s GitHub personal account by assigning the ‘Default Access’ role in the Enterprise Application in Entra ID.

Step 3 [as the new user]: Accept the invitation from the email address that is associated with the personal account.
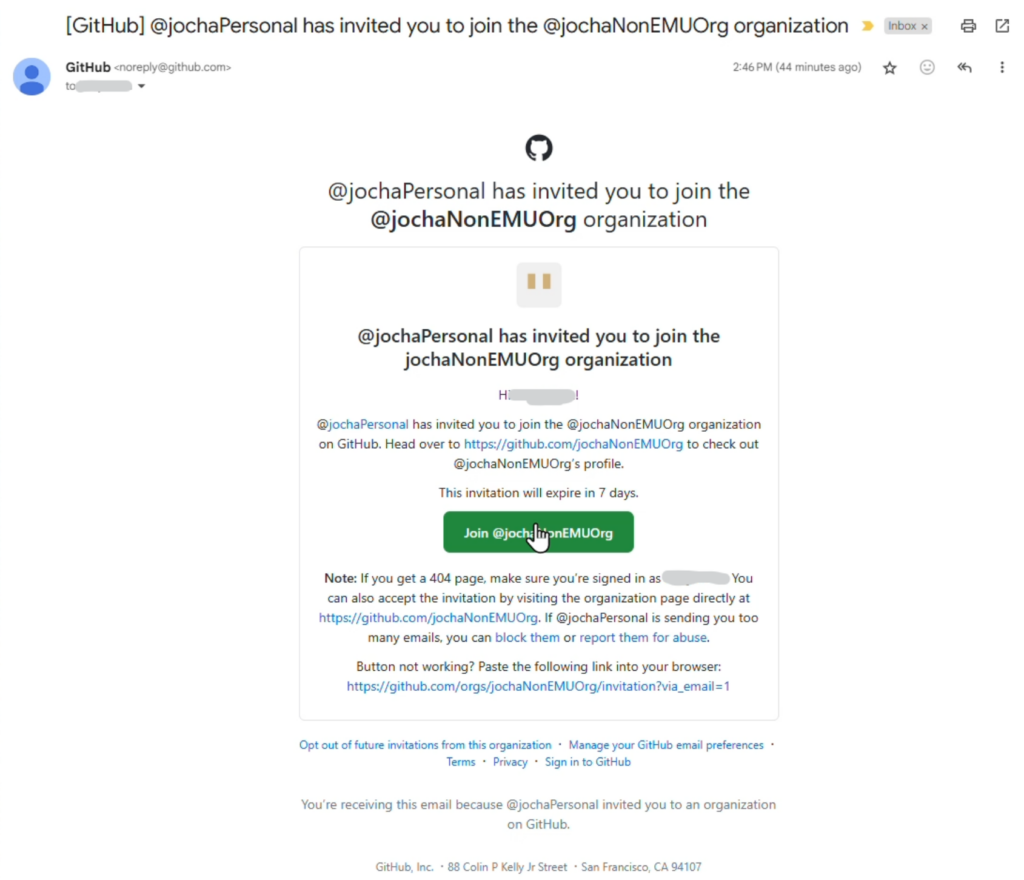
Step 4 [as the new user]: GitHub will prompt the new user to authenticate with the SAML IDP to join the organization. This is where the linking happens. The new user will need to sign in to the IDP used for SAML. Going forward, the new user will login to GitHub.com with the personal account, then go through SAML SSO login when navigating to the specific organization of the Enterprise.


Step 5 [as the new user]: The new user can then join the organization after authentication.


Conclusion
Great, the new user is now a member of the Organization that is a part of the non-EMU enterprise! Finally, to access the resources of this organization, the new user will first login through a personal account through GitHub.com first and then single signed-on through the configured IDP of the enterprise.
In conclusion, by following these steps, you ensure a secure and efficient user provisioning process with SAML authentication in GitHub Enterprise. Altogether, this setup not only simplifies user access but also enhances security by leveraging your organization’s identity provider. Implementing SAML SSO allows for seamless integration and better management of user identities across your enterprise.
Content adapted from SAML SSO Guide Part I: SAML SSO & IP Protection within GitHub Enterprise Cloud – YouTube

comment