Over the past few weeks, we’ve been exploring Microsoft Graph connectors and seen how to work smarter and more efficiently by accessing your external data sources within Microsoft 365 alongside your internal content. In this post, we will show you to securely import external content to Microsoft 365 with Microsoft Graph connectors, and how this can benefit you and your organization.
Why you should consider importing external content to Microsoft 365
By using Microsoft Graph connectors, you can import content from various external sources into Microsoft 365. This not only allows you and your colleagues to easily find relevant information in your organization from one place but also to discover new content and easily share it with your colleagues. What’s more, when you start using Microsoft 365 Copilot, importing external content to Microsoft 365 will allow Copilot to reason over more of your organization’s information, giving you more relevant responses.
Importing external content with correct permissions
Information that you store outside of Microsoft 365 is either accessible by everyone in your organization or only by a select group of people. The permissions for accessing external content are stored in the external system.
When importing content using Microsoft Graph connectors, you retrieve content and its permissions from your external system. Using this information, for each piece of content that you import, you build an access control list (ACL) and include it with the item when it’s imported to Microsoft 365.
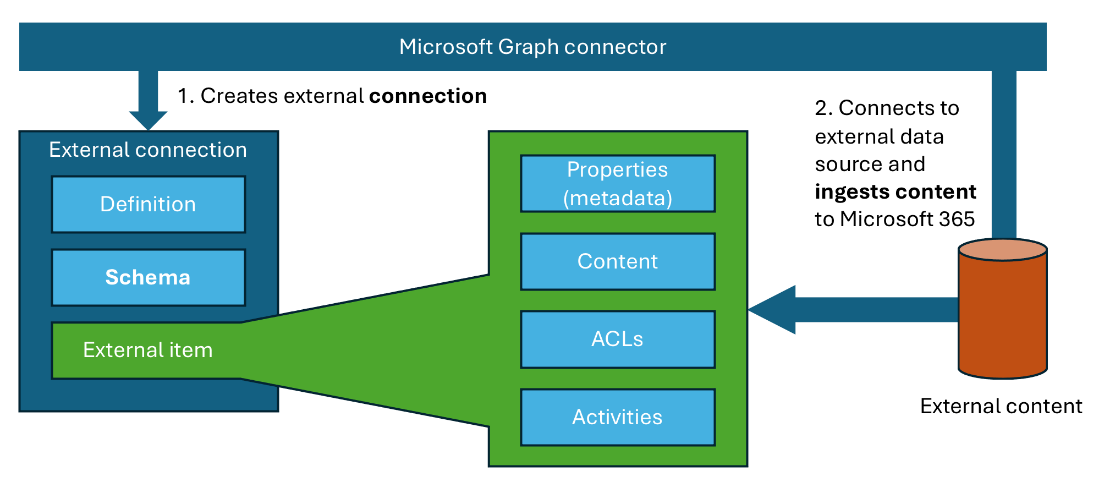
This lets you ensure that only individuals specified in the external system can access the imported content. When importing external content using Microsoft Graph connectors, you have several options to ensure that it’s accessible by the same group of people who can access it in the external system.
Anatomy of an access control list
An access control list is an array of access control entries. Each entry consists of three elements:
- Access type, which specifies if the entry is for granting or denying access to the piece of content
- Type, which specifies the type of entity described by the entry. It can be a Microsoft Entra user, Entra group, everyone in your tenant, everyone except guest users, or an external group (i.e., group that’s defined in your external system)
- Value, which identifies the entity described by the entry
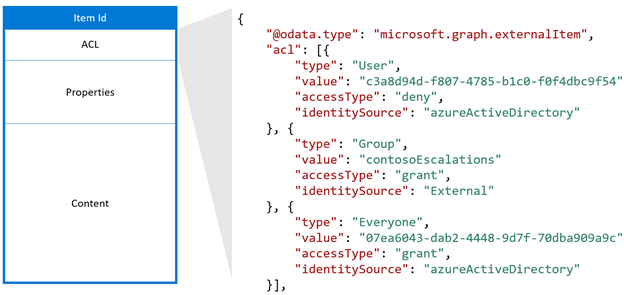
PRO TIP: Each imported item must include at least one access control entry. You can also include multiple entries to make the item accessible by multiple groups of people.
Let’s have a look at some common scenarios of how you’d ensure correct access to your imported content.
Importing content available to everyone in the organization
One of the most common scenarios is importing external content that’s available to everyone in the organization. If you’re importing such content, you can use the following access control entry on all content items:
Access type: grant
Type: Everyone
Value: Everyone
Importing content available only to specific group of people from an external system with single sign-on with Microsoft 365
If your external system has single sign-on with Microsoft 365, your external content is secured with users and groups from Microsoft Entra ID (previously Azure Active Directory). In such cases, you can define access control entries, of type User (if you’re referring to single Entra users) or Group (when you’re referring to Entra groups). You’ll configure the value to refer to the Microsoft Entra user or group, for example:
Access type: grant
Type: group
Value: Management
Importing content available only to specific group of people from an external system without single sign-on with Microsoft 365
If you’re importing content from a system that doesn’t have single sign-on with Microsoft 365, you can still ensure that the imported content is properly secured and only available to the correct individuals. In such case, you’ll define external groups which you’ll use to secure the imported content. These groups reflect memberships defined in the external system but refer to Microsoft Entra users and groups or other external groups.
For more information about working with external groups, review the documentation.
Keep your external permissions and access control lists synchronized
The external system from which you import content to Microsoft 365 contains the primary reference of permissions and who has access to what content. When building Microsoft Graph connectors, you must synchronize these permissions to your content imported to Microsoft 365 to ensure its security.
If your external system raises an event when permissions change, you can immediately update them on the external content imported to Microsoft 365. If the external system doesn’t support events, then you’ll build a frequently running process that scans for changed permissions and updates them accordingly. You should include the ability to refresh permissions on demand, which will allow you to instantaneously refresh permissions if such a need arises.
Conclusion
Microsoft Graph connectors are a powerful and versatile way to centralize content in your organization on Microsoft 365 so that you can easily find and share information with your colleagues. When importing content, you must ensure that it’s secured as defined in the external system. Microsoft Graph connectors offer you several flexible ways to define permissions on imported content to ensure that it’s only accessible by privileged individuals. Once content is imported, it’s protected by the same security and compliance policies that apply to Microsoft 365 data.
To learn more about configuring permissions on content imported using Microsoft Graph connectors, see the documentation.
Try Graph connector samples built by Microsoft and the Microsoft 365 community, to see what’s possible.
More resources:
- Visit our Microsoft 365 Dev Center
- Follow us on Microsoft 365 Developer (@Microsoft365Dev) / X for the latest news and announcements
- Check out demos and videos on Microsoft 365 Developer – YouTube
Happy coding!


0 comments