April Security Release: Patches available for Azure DevOps Server 2019, TFS 2018.3.2, TFS 2018.1.2, TFS 2017.3.1, and the release of TFS 2015.4.2
For the April security release, we are releasing fixes for vulnerabilities that impact Azure DevOps Server 2019, TFS 2018, TFS 2017, and TFS 2015. These vulnerabilities were found through our Azure DevOps Bounty Program. Thanks to everyone who has been participating in this program.
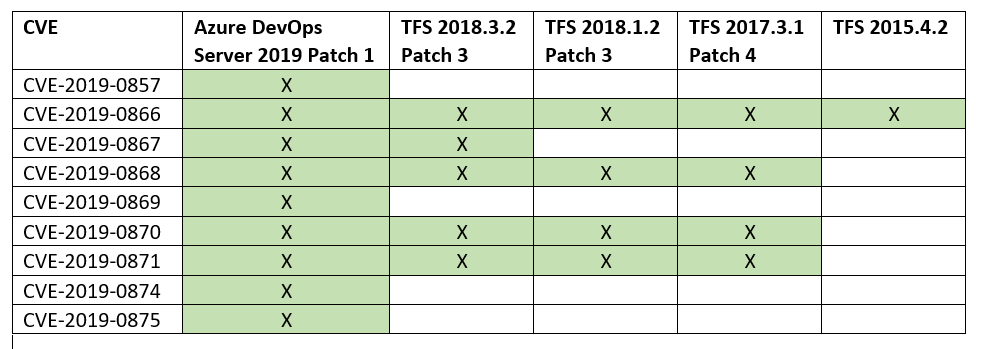
CVE-2019-0857: spoofing vulnerability in the Wiki
CVE-2019-0866: remote code execution vulnerability in Pipelines
CVE-2019-0867: cross site scripting (XSS) vulnerability in Pipelines
CVE-2019-0868: cross site scripting (XSS) vulnerability in Pipelines
CVE-2019-0869: HTML injection vulnerability in Pipelines
CVE-2019-0870: cross site scripting (XSS) vulnerability in Pipelines
CVE-2019-0871: cross site scripting (XSS) vulnerability in Pipelines
CVE-2019-0874: cross site scripting (XSS) vulnerability in Pipelines
CVE-2019-0875: elevation of privilege vulnerability in Boards
Azure DevOps Server 2019 Patch 1
If you have Azure DevOps Server 2019, you should install Azure DevOps Server 2019 Patch 1.
Verifying Installation
To verify if you have this update installed, you can check the version of the following file: [INSTALL_DIR]\Application Tier\Web Services\bin\Microsoft.TeamFoundation.Server.WebAccess.VersionControl.dll. Azure DevOps Server 2019 is installed to c:\Program Files\Azure DevOps Server 2019 by default.
After installing Azure DevOps Server 2019 Patch 1, the version will be 17.143.28804.3.
TFS 2018 Update 3.2 Patch 3
If you have TFS 2018 Update 2 or Update 3, you should first update to TFS 2018 Update 3.2. Once on Update 3.2, install TFS 2018 Update 3.2 Patch 3.
Verifying Installation
To verify if you have this update installed, you can check the version of the following file: [TFS_INSTALL_DIR]\Application Tier\Web Services\bin\Microsoft.TeamFoundation.WorkItemTracking.Web.dll. TFS 2018 is installed to c:\Program Files\Microsoft Team Foundation Server 2018 by default.
After installing TFS 2018 Update 3.2 Patch 3, the version will be 16.131.28728.4.
TFS 2018 Update 1.2 Patch 3
If you have TFS 2018 RTW or Update 1, you should first update to TFS 2018 Update 1.2. Once on Update 1.2, install TFS 2018 Update 1.2 Patch 3.
Verifying Installation
To verify if you have this update installed, you can check the version of the following file: [TFS_INSTALL_DIR]\Application Tier\Web Services\bin\Microsoft.TeamFoundation.Server.WebAccess.Admin.dll. TFS 2018 is installed to c:\Program Files\Microsoft Team Foundation Server 2018 by default.
After installing TFS 2018 Update 1.2 Patch 3, the version will be 16.122.28801.2.
TFS 2017 Update 3.1 Patch 4
If you have TFS 2017, you should first update to TFS 2017 Update 3.1. Once on Update 3.1, install TFS 2017 Update 3.1 Patch 4.
Verifying Installation
To verify if you have a patch installed, you can check the version of the following file: [TFS_INSTALL_DIR]\Application Tier\Web Services\bin\Microsoft.TeamFoundation.Server.WebAccess.Admin.dll. TFS 2017 is installed to c:\Program Files\Microsoft Team Foundation Server 15.0 by default.
After installing TFS 2017 Update 3.1 Patch 4, the version will be 15.117.28728.0.
TFS 2015 Update 4.2
If you are on TFS 2015, you should upgrade to TFS 2015 Update 4.2 with the ISO or Web Install. For TFS 2015 Update 4.2 Express, you can upgrade with the ISO or Web Install. This is a full upgrade and will require you to run the Upgrade Wizard.

 Light
Light Dark
Dark
27 comments
why do I need to login to see the CVEs but a normal Live account does not work?
This is an error. We are working on updating the links to public versions.
The links are updated now. Sorry about that.
For TFS 2015 Update 4.2 is there an express version available? tfsexpress2015.4.2.exe
I just updated the post with the links for TFS 2015 Update 4.2 Express. The web install is at https://go.microsoft.com/fwlink/?linkid=844070. Thanks!
Thanks for the link. The install failed with “A setup package is either missing or damaged.” Since this is a web installer looks like its failing to download some packages during install. thanks,
I’m taking a look. In the meantime, can you get unblocked by downloading the ISO?
Had the same issue with the TFS 2015 Web Install, had to use the ISO to update without the error.
Tried to apply the patch on a TFS2018 Update 3.2 Patch 2:Error patching files: System.UnauthorizedAccessException: Access to the path ‘C:\Program Files\Microsoft Team Foundation Server 2018\Application Tier\TFSJobAgent\Microsoft.TeamFoundation.DistributedTask.Orchestration.Server.dll’ is denied.
The current version of C:\Program Files\Microsoft Team Foundation Server 2018\Application Tier\Web Services\bin\Microsoft.TeamFoundation.WorkItemTracking.Web.dll is 16.131.28626.3 (I applied yesterday tfs2018.3.2patch2.exe)
Hi Daniel,
For TFS 2018 Update 3.2, it should be patch 3. Can you confirm you installed tfs2018.3.2patch3.exe, not patch2? Are you still having the System.UnauthorizedAccessException issue?
Hi, I just installed this patch on two of our test Azure Devops 2019 servers. On both servers the installation succeeded but it encountered a timeout exception while waiting for the application pool to have succesfully stopped. It doesn’t seem to correctly detect that the pool has stopped so it’ll hit the timeout. When retrying it’ll instantly detect that the pool has stopped and continue with applying the patch.
Hello Corné,
I found out some information from my collegue, Matt.
Sorry that you ran into problems with the install. There are some rare cases where we don’t correctly detect that everything has stopped. In those cases, re-running the patch is the correct response, and it will correctly update the files and then restart the server.
When will be the groundbreaking feature implemented for an unattend installation from patches?
🙂 We expect it to be available for the May security release.
@Erin, will these patches included in the ISO images downloadable from MSDN etc? If so, will take a long time? TIA
Hi Giulio,
No, these won’t be included in the MSDN/VS Subscription ISOs. You’ll have to apply these patches over the installations you do with the VS subscription ISOs.
But only the latest patch, all predecessors are included, right?
Correct. All of the patches include all the fixes from previous patches.
Hello Erin,
Thank you for the detailed description. I have a question which may sound silly. But are these patches applicable on the cloud or on the on prem environment?
Thank you
Hi Aditya,
These are only applicable to the on premises environments. All vulnerabilities that impacted our cloud service have already been addressed, so no action is needed for the service.
Hello Erin,
Thank you so much for the prompt response.
I ran this against our server with 2017 3.1 and we now get an error starting up the TFS administration console saying that “There was an exception while launching the Team Foundation Administration Console: Could not load file or assembly ‘Microsoft.TeamFoundation.Framework.Server, Version=11.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a’ or one of its dependencies. The located assembly’s manifest definition does not match the assembly reference. (Exception from HRESULT: 0x80131040)”. Any thoughts?
Everytime I run one of these patches for 2017 the output is a bunch of “Waiting on process NNNNN (XXX seconds elapsed)” for several minutes, sporadic exceptions, waiting for the pool to stop for several more minutes, a final flurry of activity I suspect is that actual update running, and then the installer completes. I expect it to take several minutes and throw several exceptions and yet still ‘succeed’.
Are the 2018 and 2019 installers markedly better than the 2017 installer in this regard? Is this motivation to move to 2019 or just what I should expect with these installs?
Why you not update version in console TFS?..