You can now self-regenerate new client secrets as needed for apps made on top of the Azure DevOps’ OAuth platform. A valid, active client secret is critical for getting a refresh token to continue using your app. Once the secret has expired, you will also no longer be able to get access and refresh tokens needed to access Azure Devops APIs through this app.
Why is this important?
Client secrets have historically expired 5 years after the original app creation date. This new feature is useful for folks to get ahead of their app expiration and replace any soon-to-expire client secret before it runs out and causes unintended app service outages.
Alternatively, if a client secret has been leaked, app owners are encouraged to immediately revoke their existing client secret and regenerate a new one to prevent any unauthorized usage of their app.
Previously, app owners were required to reach out to Azure DevOps customer support to get their client secrets renewed for another 5 years. This is not necessary anymore, as app owners can now choose to renew their client secrets whenever they like on their own time. This gives them the freedom to update the client secret more regularly than the default 5 years as desired for your company’s compliance needs.
How to regenerate the client secret?
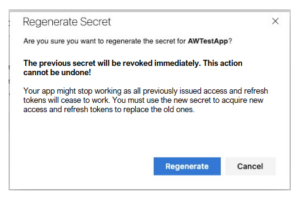
You can regenerate a client secret by finding the application page on your profile here. A new “Regenerate Secret” button and secret expiration date are now available.
When you generate a new client secret, the previous client secret will expire and so will all previously minted access tokens for that app. Please bear that in mind when you schedule any necessary outage time while your new secret replaces your old one.
What about for new OAuth apps?
This new functionality is specific to Azure DevOps OAuth apps and is unrelated to Entra OAuth apps created via the Microsoft Identity platform.
We recommend all net new apps explore using the Entra OAuth app platform instead, which is being actively developed with new functional and security features regularly. Existing Azure DevOps OAuth app owners are also encouraged to explore migrating to Entra OAuth for their apps, if that’s a viable option. You can learn more about OAuth with Azure DevOps in our guide to OAuth here.



It’s important to mention that this functionality is specific to Azure DevOps OAuth apps and doesn’t apply to Entra OAuth apps created via the Microsoft Identity platform. If you’re working on new OAuth apps, it’s recommended to consider using the Entra OAuth app platform, which is actively developed with new functional and security features regularly. Existing Azure DevOps OAuth app owners are also encouraged to explore migrating to Entra OAuth for their apps if it’s feasible.