Defending Federal Systems with the Microsoft Sentinel Threat Analysis & Response Solution
This blog is jointly authored by Lili Davoudian, Senior Product Manager, Cloud & AI Security; Ashwin Patil, Senior Security Researcher, Microsoft Threat Intelligence Center; and Ron Marsiano, Senior Product Manager, Microsoft Sentinel.
With the growing need for federal agencies to evaluate coverage of respective threat detection capabilities along with the need for adaptive solutions to evaluate and recommend analytics coverage within the MITRE ATT&CK® framework – Microsoft now offers a singular place to manage your security coverage with the MITRE ATT&CK® blade.
Threat hunting programs also require dynamic threat modeling capabilities to understand where threats are maneuvering against workloads. Visibility is only half the battle, as incident response and remediation are required to mitigate threats ensuring organizations evolve defenses during each observed incident.
Now, our Microsoft Sentinel: Threat Analysis & Response Solution takes this a step further with two new workbooks designed to support development of threat hunting programs and dynamic threat modeling designed to identify, respond, harden, and remediate against threats.
Watch the demo:
In this video, we discuss and demo the Microsoft Sentinel: Threat Analysis & Response Solution
Key benefits
- Proactive threat modeling (red vs. blue)
- Quantifiable framework for building threat hunting programs
- Monitoring & alerting of security coverage, threat vectors, and blind spots
- Response via security orchestration automation and response (SOAR) playbooks
- Remediation with cloud security posture management (CSPM)
- Compliance alignment to NIST SP 800-53 controls
Microsoft Sentinel: Threat Analysis & Response Solution content
Solution content:
Threat Analysis & Response Workbook
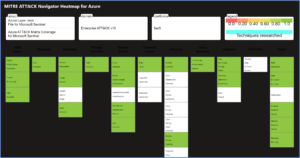
Designed by the Microsoft Threat Intelligence Center, this workbook provides the foundation for building threat hunting programs. This workbook features recommended steps for getting started including resources for deploying analytics rules and hunting queries. Data Source Statistics provides an overview of which logs are ingested from respective sources which provides a starting point for determining utility of respective analytics rules. The Microsoft Sentinel GitHub section provides an overview of available analytics by alignment to respective tactics/techniques. MITRE ATT&CK Navigator Heatmap provides an assessment of coverage by tactic and technique areas which is valuable for evaluating the efficiency of organizational threat hunting programs.
Threat Analysis & Response Workbook
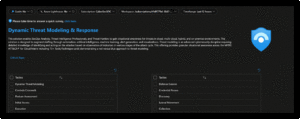
Dynamic Threat Analysis & Response Workbook
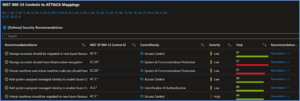
The Dynamic Threat Analysis & Response Workbook dynamically assesses attacks to your on-premises, cloud, and multi-cloud workloads. Attackers are categorized by the MITRE ATT&CK for Cloud Matrix and evaluated against Microsoft Sentinel observed Analytics and Incidents. This provides pivots to evaluate attacks against specific users, assets, attacking IPs, countries, assigned analyst, and detecting product. Each tactic provides a respective control area comprised of technique control cards. Technique Control Cards provide details of establishing coverage, evaluation of observed attacks, and defense recommendations aligned to NIST SP 800-53 controls. Observed attacks are addressed via Microsoft Sentinel Incidents for Investigation, Playbooks for Response, MITRE ATT&CK blade for Coverage, and Microsoft Defender for Cloud for Remediations.
Dynamic Threat Modeling & Response Workbook
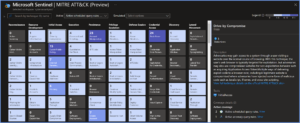
Microsoft Sentinel: MITRE ATT&CK blade
MITRE ATT&CK is a publicly accessible knowledge base of tactics and techniques that are commonly used by attackers and is created and maintained by observing real-world observations. Many organizations use the MITRE ATT&CK knowledge base to develop specific threat models and methodologies that are used to verify security status in their environments. Microsoft Sentinel analyzes ingested data, not only to detect threats and help you investigate, but also to visualize the nature and coverage of your organization’s security status.
Microsoft Sentinel: MITRE ATT&CK blade
Get started today
To get started, go to your Azure or Azure Government portal to access the solution:
- Microsoft Sentinel > Content Hub > Search “Threat Analysis & Response” > Install
- Review Workbooks (“Dynamic Threat Modeling & Response” & “Threat Response & Analysis”)
- Microsoft Sentinel > MITRE ATT&CK
- Review Coverage
- See ReadMe for prerequisites, feature details, and deployment guidance
Learn more about threat hunting with Microsoft Security
- Understand security coverage by the MITRE ATT&CK® framework
- Joint forces – MS Sentinel and the MITRE framework
- MITRE ATT&CK® mappings released for built-in Azure security controls



 Light
Light Dark
Dark
1 comment
It would be helpful to have a version of this that is focused on the TSA security directives for various critical industries