Ever since MCP launched, every customer has asked the same thing: “How does a private MCP registry actually work, and how do we configure it for our enterprise?”.
So today, on a snowy, freezing Friday in Zurich, I grabbed a coffe, opened the GitHub docs, dove into Azure API Center portal, and decided to write the blog I wish already existed.A few hours (and quite a few sighs) later, here I am. The docs are great but they definitely don’t cover all the tiny quirks, hidden settings, and errors you’ll hit along the way.
What did the journey look like?
- 📚 Reading way too many docs
- ✅ A data API that seemed to work
- 🔒 Mysterious 401 Unauthorized responses
- 🧊 A Save + publish button permanently frozen in “Nope” mode
- 🚫 404 Not Found and VS Code insisting the registry “does not support version v0.1”
- 🤯 And finally… the magical, undocumented discovery of
/workspaces/default/v0.1/servers
This post is the guide I desperately needed: a clean, step-by-step setup plus every weird error and how to fix it. Enjoy!
Two Options: Pick Your MCP Registry Adventure 🎒
To make an MCP registry that GitHub Copilot can actually talk to, you need two non-negotiables:
- A proper MCP Registry endpoint that follows the v0.1 specification
- CORS enabled so Copilot/VS Code can reach it from the browser environment
And you’ve got two ways to get there:
Option 1: Self-hosted MCP Registry
Spin up your own service that fully implements the v0.1 MCP Registry spec and handles all the CORS requirements.Great for full control but not so great if you’re not in the mood to maintain yet another service.
Option 2: Azure API Center (the easy path)
Azure API Center comes with:
- ✔️ Built-in support for the v0.1 MCP Registry spec
- ✔️ CORS configured out of the box
- ✔️ A nice UI for managing MCP servers
- ✔️ Zero infrastructure to run yourself
So for this blog (and for our sanity), we’re going with Azure API Center.
What We’re Building 🚀
We’re setting up a private MCP registry using Azure API Center and wiring it so GitHub Copilot and VS Code only recognize and use the MCP servers we list there.
In other words:
- Azure API Center becomes our private MCP registry
- GitHub Copilot + VS Code automatically discover the approved MCP servers
- Only those servers are allowed to run on the client

Step 1: Create Your Azure API Center Instance
In the Azure portal:
- Search for “API Center” and Click + Create.
- Fill in:
- Subscription / Resource group: choose your usual.
- Name: e.g.
private-mcp-registry. - Region: e.g.
East US. - SKU: Free/Standard (Free is fine to experiment).
3. Click Review + create → Create.
Once deployment is done, open the resource and note the data-plane endpoint, which looks like:
https://private-mcp-registry.data.eastus.azure-apicenter.ms
Note: Please make sure that you are using data endpoint and not the portal endpoint
✅ data endpoint: https://private-mcp-registry.data.eastus.azure-apicenter.ms
🚫 portal endpoint: https://private-mcp-registry.portal.eastus.azure-apicenter.ms
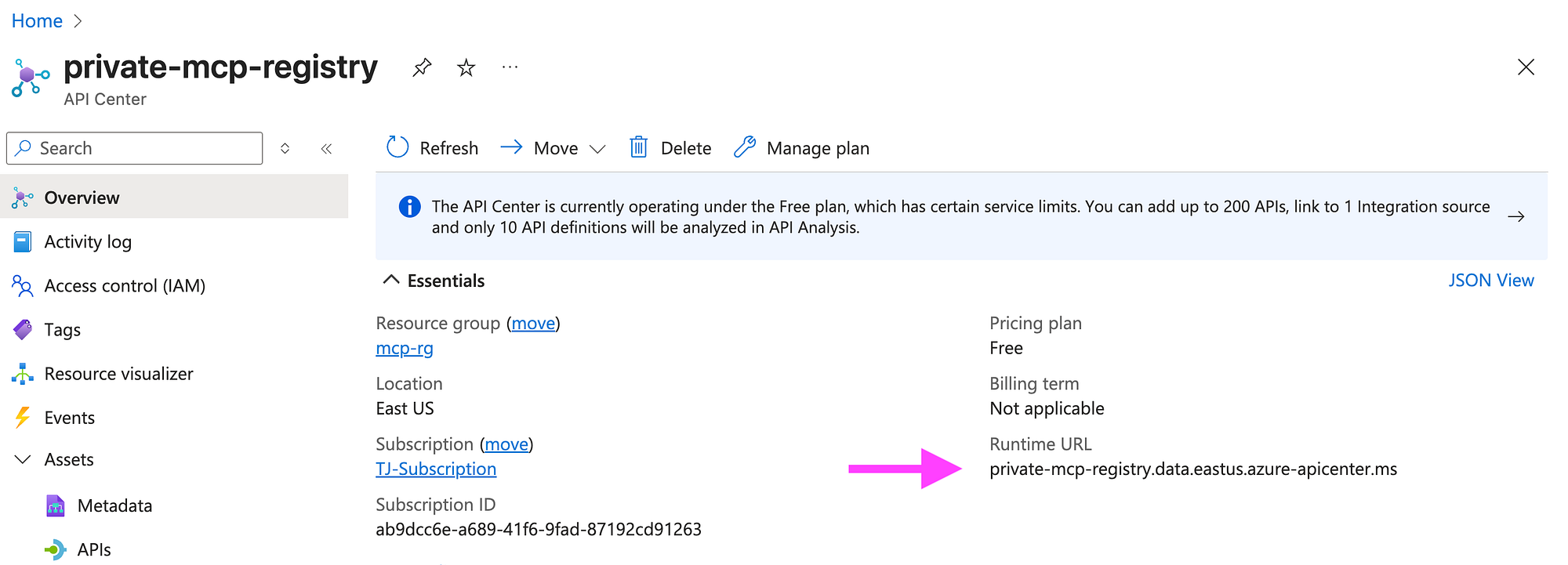
This host is where the MCP registry will live (we’ll refine the path later).
Step 2 : Register MCP Servers
API Center gives you two options:
1️⃣ Create and expose your own MCP server through API Center, or
2️⃣ Use one of the pre-listed MCP servers available in the Discovery section.
If you want to register your own MCP server, go to Assets → APIs → Register an API, fill in the details, and create a new MCP-type API.
Or, if you prefer the easier path, you can use the preview Discovery feature, which lets you add ready-made MCP servers to your registry with a single click. Just go to Discover → MCP (preview) on the left panel.
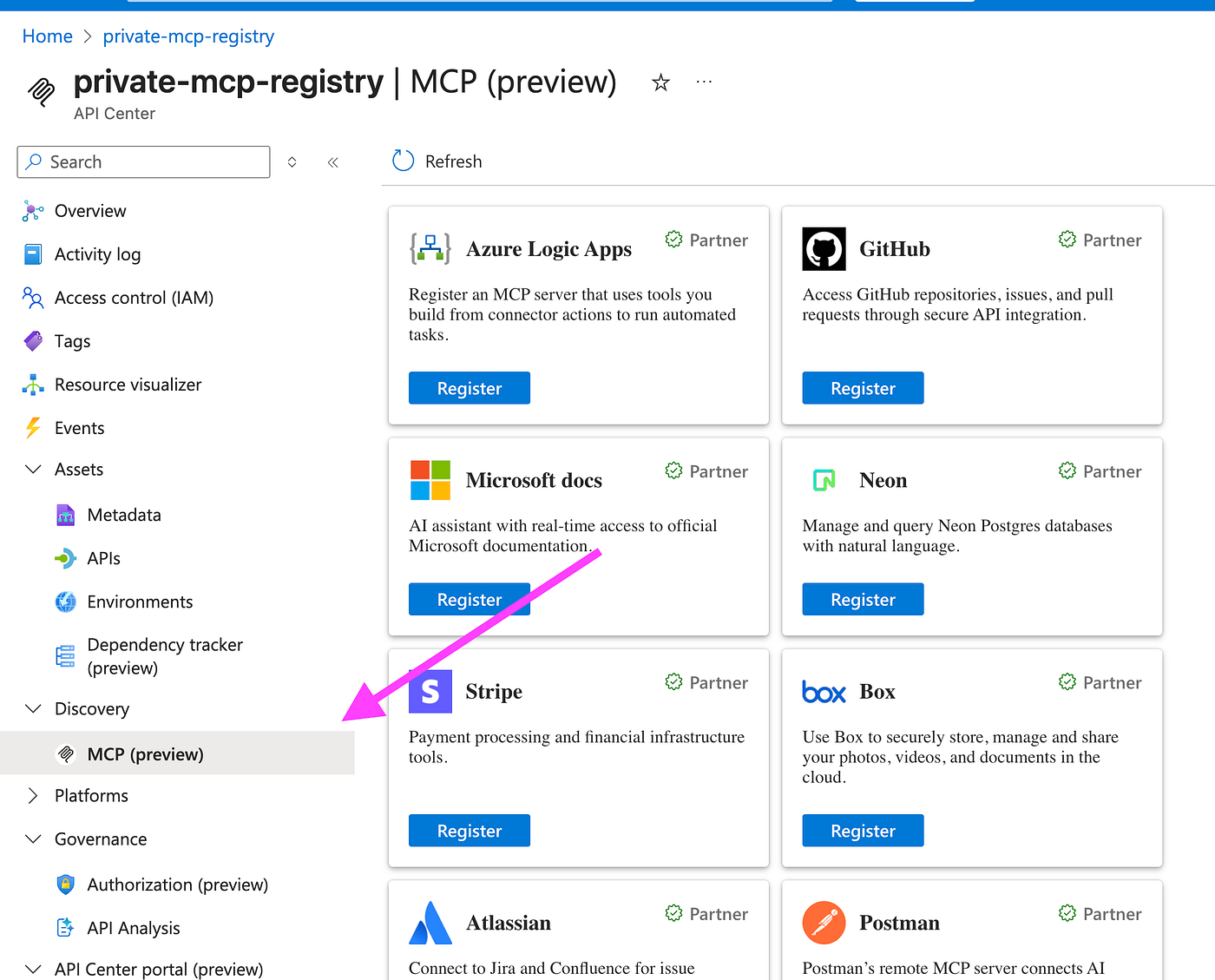
For this blog, I added “Microsoft Docs” and “Atlassian”. Once saved, these MCP servers become part of your registry inventory, and you can view them under Assets → APIs. For lifecycle management, you can also assign each server to an environment such as production, testing, or development.
Step 3: Enable the API Center Portal and Anonymous Access
This is where the fun began for me.
as per GitHub docs, “to ensure GitHub Copilot can fetch your registry, in the visibility settings of your API Center, allow anonymous access”.I expected a neat “Allow anonymous access” checkbox somewhere obvious. Instead, I got:
- A greyed-out “Save + publish” button and
- A
/v0.1/serversendpoint that always returned 401.
Here’s the actual order that works.
Turn on the API Center portal (so Save + publish works)
- In your API Center resource, in the left menu, find “API Center portal”→ Settings.
- Go to the Identity provider tab.
- Click Start set up (or Quick setup).
- Complete the wizard
- Click Save + publish.
Until you do this, the global Save + publish button on the portal settings tends to be disabled or useless.
Enable anonymous access to the data API
- Still under API Center portal → Settings, go to the API visibility tab.
- Look for “Anonymous access”.
- Turn it On.
- Click Save + publish again.
What this does:
- It allows unauthenticated read access to the data plane API, so your MCP clients (GitHub, VS Code) can read the registry without dealing with Azure AD tokens.
- If anonymous access is off, you’ll see 401 Unauthorized when you hit the registry endpoints.
Step 4: Find the Real MCP Registry Endpoint
This was the “aha!” moment.At first, I assumed the registry was at: https://private-mcp-registry.data.eastus.azure-apicenter.ms/v0.1/servers
Calling that gave me: “HTTP/1.1 404 Not Found” and VS Code logs like: The service at https://private-mcp-registry.data.eastus.azure-apicenter.ms does not support version v0.1. Service returned status 404.
The missing piece: the registry endpoints live under a workspace.
API Center includes a default workspace, and your MCP registry endpoint must include the workspaces/default segment in the URL. If you prefer, you can create additional workspaces: just make sure to adjust the URL accordingly.
If you’re following this blog with my setup, your MCP registry endpoint will look like this: “https://private-mcp-registry.data.eastus.azure-apicenter.ms/workspaces/default/v0.1/servers”
Run this:
curl "https://private-mcp-registry.data.eastus.azure-apicenter.ms/workspaces/default/v0.1/servers"If everything is configured correctly, you should see:
{
"servers": [
{
"server": {
"$schema": "https://static.modelcontextprotocol.io/schemas/2025-09-29/server.schema.json",
"name": "msdocs-mcp-server",
"description": "AI assistant with real-time access to official Microsoft documentation.",
"version": "Original",
"remotes": [
{
"type": "sse",
"url": "https://learn.microsoft.com/api/mcp"
}
]
},
"_meta": {
"io.modelcontextprotocol.registry/official": {
"status": "active",
"createdAt": "2025-11-21T10:57:54.753206+00:00",
"updatedAt": "2025-11-21T10:58:01.1231068+00:00",
"isLatest": true
},
"x-ms-id": "b8c6e77d-f266-4a0a-a341-cc9e97c15280"
}
},
{
"server": {
"$schema": "https://static.modelcontextprotocol.io/schemas/2025-09-29/server.schema.json",
"name": "atlassian-mcp-server",
"description": "Connect to Jira and Confluence for issue tracking and documentation.",
"version": "Original",
"remotes": [
{
"type": "sse",
"url": "https://mcp.atlassian.com/v1/sse"
}
]
},
"_meta": {
"io.modelcontextprotocol.registry/official": {
"status": "active",
"createdAt": "2025-11-21T10:58:13.1934455+00:00",
"updatedAt": "2025-11-21T10:58:18.6788839+00:00",
"isLatest": true
},
"x-ms-id": "f9894e12-64f9-49ca-84a1-d01fcd4278c8"
}
}
],
"metadata": {
"count": 2
}
}The key is the shape: <data endpoint> / workspaces / <workspaceName> / v0.1 / servers
Step 5 : Configure GitHub’s MCP Registry URL
Now that the endpoint works, we need to wire it into GitHub so Copilot and VS Code use it.
⚠️ Important: in GitHub’s config, you do not include /v0.1/servers.You point it at the workspace base URL, and the GitHub will append /v0.1/servers.
In your GitHub Enterprise or org settings:
- Go to Enteprise → AI Coontrols →MCP
- Find the MCP Registry URL field.
- Set it to:
https://private-mcp-registry.data.eastus.azure-apicenter.ms/workspaces/default - Choose your MCP policy:
-
- Allow all MCP servers, or
- Registry only (only servers from this registry).
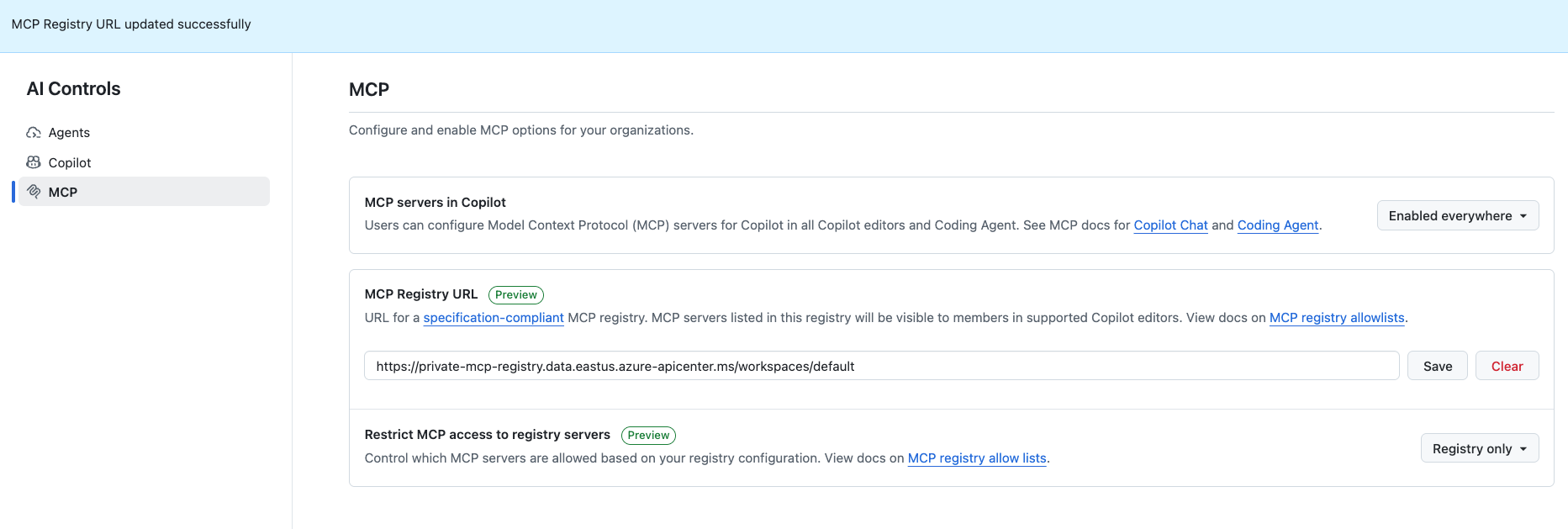
Behind the scenes, VS Code will now call:
https://private-mcp-registry.data.eastus.azure-apicenter.ms/workspaces/default/v0.1/serversStep 6: Test in VS Code
Once the enterprise settings have propagated, open VS Code and try accessing your previously installed MCP servers, you’ll notice a yellow exclamation mark on them.
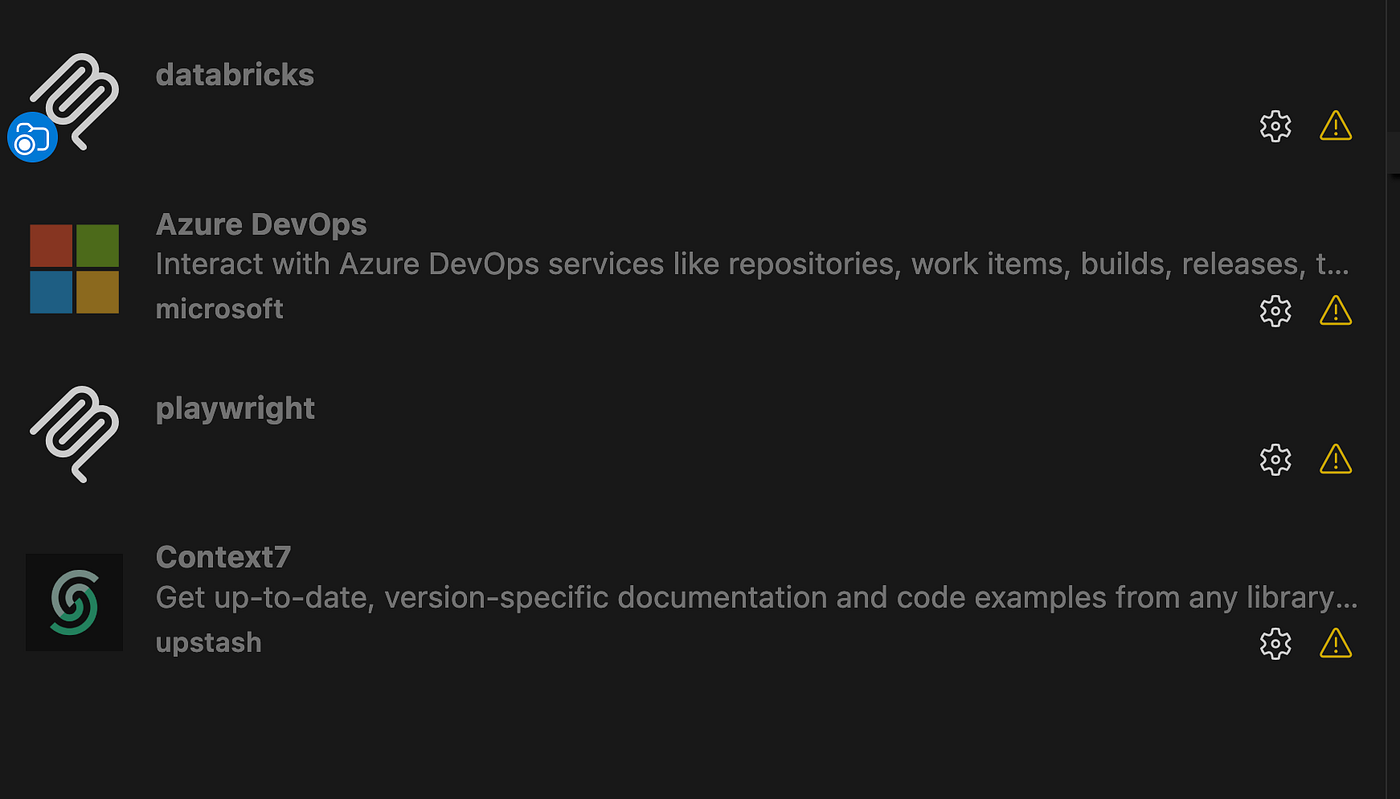
When you select an MCP server that isn’t part of the private registry enforced by your GitHub policies, VS Code will show a warning message:
“This MCP server is disabled because it is configured to be disabled in the editor.”
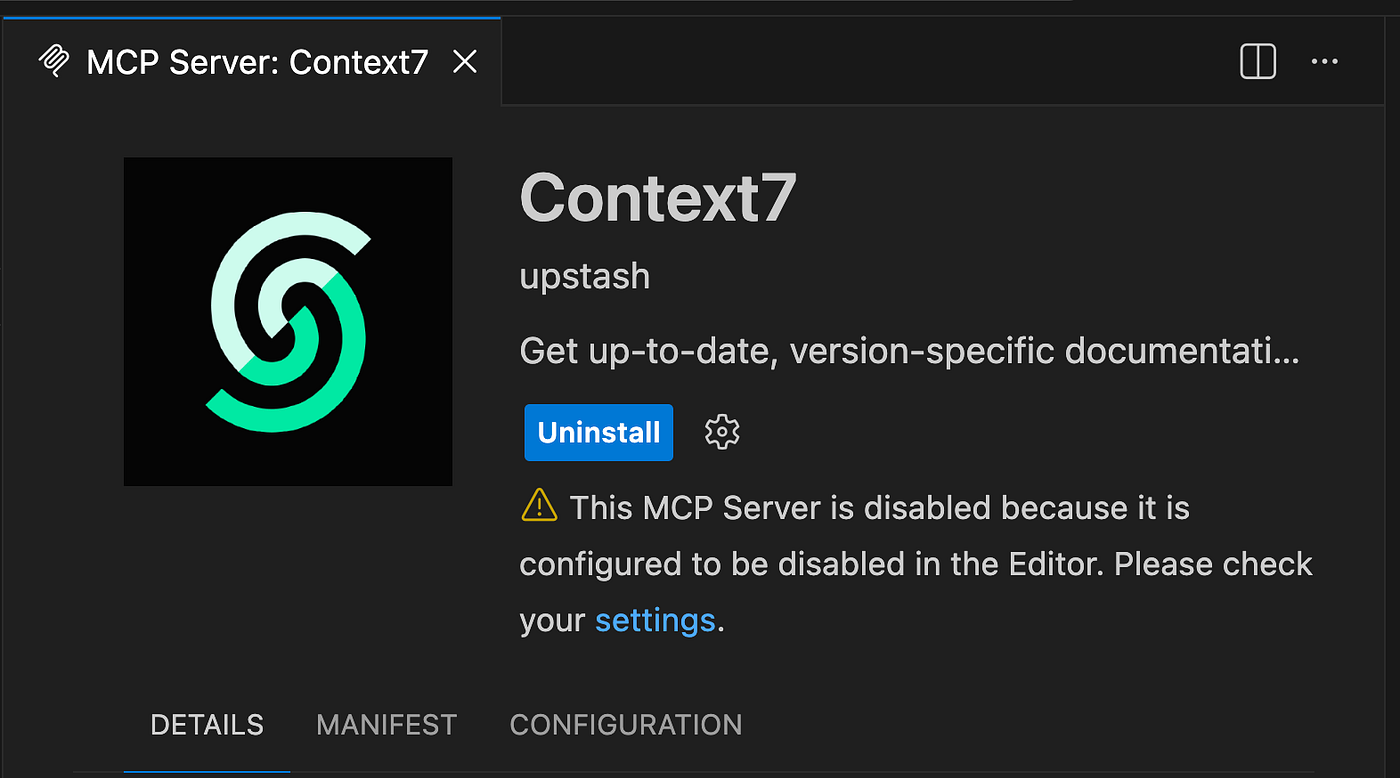
When you open the MCP access settings in VS Code, you’ll see that “registry” is selected as the control method for installing MCP servers. This setting is enforced by your GitHub policies, so the user cannot toggle it: the option is greyed out.
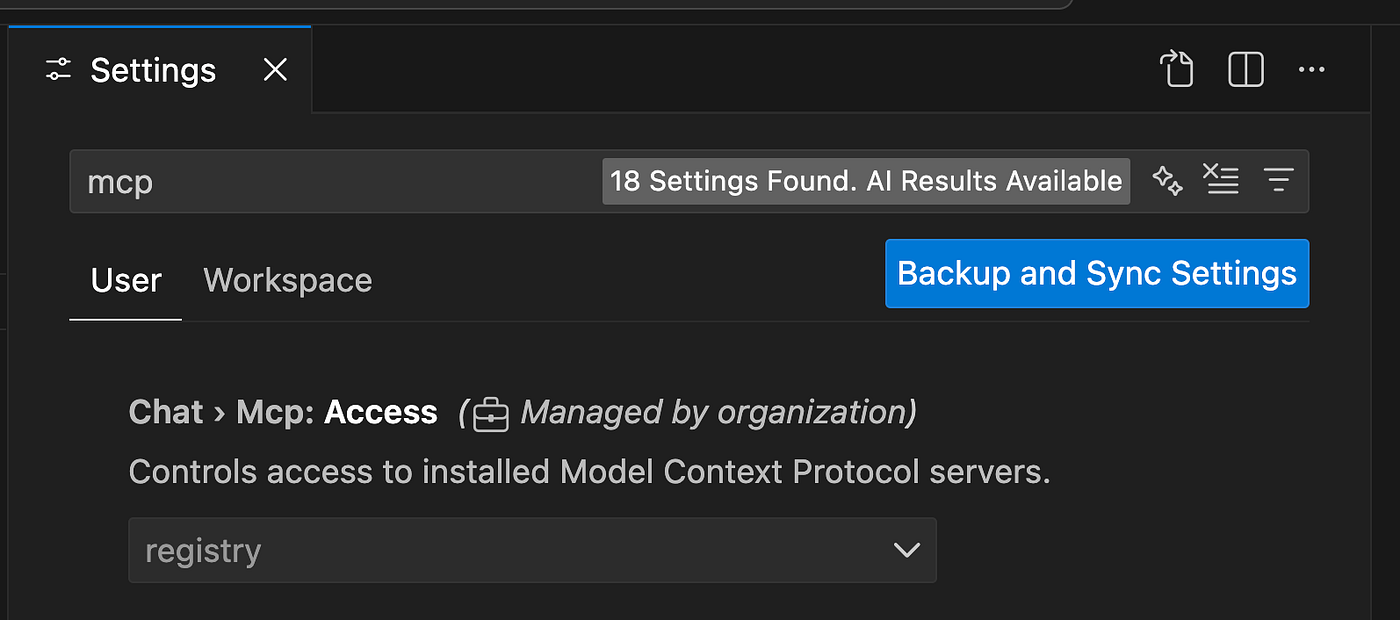
Now let’s check which MCP servers are available for installation in VS Code. When you type @MCP in the extensions section, instead of seeing the full list of servers, you’ll only see the two MCP servers we exposed through Azure API Center and included in our private MCP registry.
And to double-confirm that these MCP servers are coming from your registry, open the Output pane in VS Code and select the “Window” channel. You’ll see the registry URL configured from Azure API Center, that’s where the server list is being fetched from.
In the end, we reached our goal: a fully working private MCP registry in Azure API Center, with two MCP servers securely exposed to GitHub and successfully enforced in VS Code.
Note: If you don’t see the correct registry being picked up, simply restart VS Code and try again.
Summary
Setting up a private MCP registry with Azure API Center is absolutely possible today, and once you know the correct workspace-scoped endpoint, things work smoothly with GitHub Copilot and VS Code. However, keep in mind that the Azure API Center registry endpoint is public when anonymous access is enabled. Currently, this is acceptable because Copilot integration depends on unauthenticated access. Even so, the ideal long-term approach is a private, authenticated MCP registry endpoint.
This capability isn’t supported yet, but I fully expect GitHub to introduce authentication and private-endpoint support in the near future. Until then, users can continue to rely on the public endpoint model.
Alternatively, if you need full control right now, a self-hosted MCP registry offers the most flexibility. In exchange, you’ll need to implement the v0.1 MCP Registry specification yourself and also ensure that CORS and endpoint behaviors are properly configured
Hopefully this guide saves you the hours I spent chasing 401s, frozen buttons, and mysterious 404s and helps you get your MCP registry up and running without the drama. Happy building! 🚀
Troubleshooting
| Issue | Solution |
|---|---|
| 401 Unauthorized | Verify you have the correct user role on the Azure API Center resource. |
| Save + Publish Button Greyed Out | Enable anonymous access to the APIs |
| 404 Not found | MCP registry endpoint must include the workspaces/default segment in the URL |
| 404 Not Found | You are using data endpoint and not the portal endpoint
✅ data endpoint: https://private-mcp-registry.data.eastus.azure-apicenter.ms 🚫 portal endpoint: https://private-mcp-registry.portal.eastus.azure-apicenter.ms |





Недропользование — это направление деятельности, связанный с освоением природных ресурсов.
Оно включает разведку полезных ископаемых и их рациональное использование.
Эта отрасль регулируется нормативными актами, направленными на охрану окружающей среды.
Эффективное управление в недропользовании способствует экономическому росту.
оэрн
A nice gotcha (or bug, pls fix). If you leave the “Description” field empty in the MCP Server configuration (so directly under API Center – APIs – Overview), then in the VS Code extension, the MCP server won’t be visible at all.
Thanks e . I will pass this on to the product team . Hopefully we can get a fix asap.
I believe I followed this correctly, but when running @mcp, I see no MCP servers listed. Also, when I go to my API center website, select an MCP server, and click to Install in Visual Studio Code, the MCP server is installed, but it has an “!” saying that the MCP server is not allowed. Accessing the data.westeurope.azure-apicenter.ms/workspaces/default/v0.1/servers URL for the site does display JSON list of the MCP servers. The URL listed in GitHub Copilot is the data.westeurope.azure-apicenter.ms/workspaces/default URL. Any thoughts?
Hey Alex, if you are getting the right json on the workspaces/default/v0.1/servers that means API center is configured correctly. On the GitHub Side if you have configured the policy then restrat your vscode and policy should be working as described in the Blogpost. I am not 100% sure what’s your question is ?
I’ve been searching for a month for the missing link to get this working and this did the trick. I can’t thank you enough for posting this.
Thats amazing Chris …happy to get that positive feedback 🙂
Also a big thanks from me, spend 3 hrs to figure this out without luck and your tip on the workspace made tit work for me. Thx for taking the time to publish this.
Great Article. If you are looking for a complete sample to expose an API using MCP With Azure APIM and API Center (bicep files included), please look at my repository https://github.com/bmoussaud/mcp-azure-apim
Daamn, I thought I could protect the endpoint from totally public accessibility by making it reachable only through a VPN connection.
The registry can be on a private network as long as the developer’s machine running e.g VS Code can reach it.The registry URL just needs to be reachable from wherever the IDE is running. GitHub’s servers never need to access it.
So, what’s really missing for me is just having Private Endpoint support for API Center, or just some basic firewall support. This way we can have it private (but still anonymous inside the network, which is fine in 99% of cases). Now I’m thinking of just continuously copying over the registry definition to something inside our network, crazy to even have to think of such workarounds if you think about all the features API Center already has!
HI TJ,
thanks for sharing this interesting post.
So if I understand it correctly, even if I go for for a self-hosted – private MCP registry, I need to open to internet in anonymous mode to allow GitHub’s servers to access it.
If this is true, I don’t see currently any advantage in having it self-hosted.
Can you be please more precise when this connection between GitHub servers and APIC can be completely private?
Thanks
Alessandro
Hey Alessandro,
What i understood from the product team is that the connection is between Client and the registry. GitHub provides a policy to define a registry URL and enforces that policies on copilot side.
So self hosting doesnt have any clear advantage. APIC makes it easy and fast to provide V0.1 specificaiton JSON thats important for registry format. Also you can create your own MCP serves and host is on Azure and expose it via APIC.
So, if the connection is between IDE and MCP registry, I don’t need to have the MCP registry open to internet and anonymous to allow Github’s Servers to reach it.
Is it correct? In such case the private registry will really be private.