Six tips for securing identity in the cloud
This 3-part blog series on security in Azure Government was co-authored by Robert Jaffe, Sr. Program Manager, and Diego Lapiduz, Chief Information Security Architect, with Microsoft Azure Global Government.
Over the last year, as modernization has accelerated, we’ve started to see many customers turning to cloud services as an asset in fighting evolving cybersecurity threats. In this three-part series on Azure Government security, we’ll cover some of the top reasons why and provide guidance on best practices for securing your Azure Government resources.
This first blog: ‘Six tips for securing identity in the cloud’ provides guidance and resources on the specific actions you can take to create more secure identity management within your agency or organization.
Background on Azure Government security:
Azure Government helps you gain unmatched security. Microsoft invests more than $1B a year and employs more than 3500 security experts to protect your information. Our security promise has three components:
- The first component is the secure foundation of Azure. This includes all the security we provide in the physical datacenters from structural security to biometric security to infrastructure, spanning the full range of best practices from preventing DDoS attacks to operational security providing the minimum just-in-time access for the minimum number of employees.
- Azure includes built-in security controls across a breadth of services across identity, network, compute, data and apps that enable comprehensive threat protection and security management. It’s important to implement these native tools, such as Azure Security Center, to rapidly improve your security posture.
- Finally, Microsoft offers threat protection informed by trillions of diverse signals we receive every day from variety of sources. For example, more than 1.2B devices scanned or more than 750M+ Azure user account authentications. This volume of data is unprecedented, and these insights are integrated into our security solutions to help you mitigate threats faster.
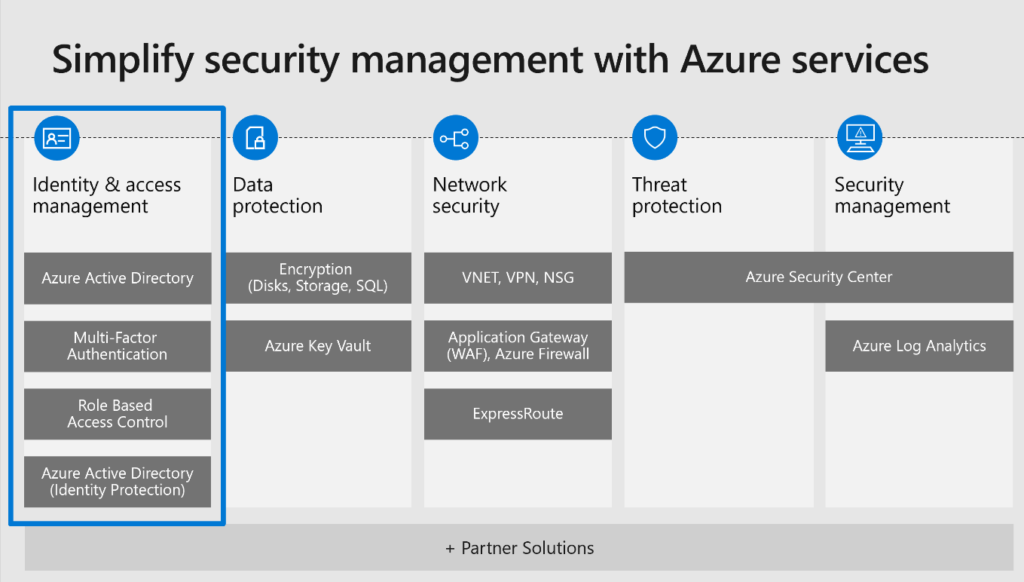
The diagram above provides a view into the built-in security controls in Azure. Let’s look first at identity and access management:
Azure Active Directory helps you enhance security, simplify access, and set smart policies with a single identity platform. For example, you can implement secure single sign-on for any application faster, more easily, and from any device.
This identity platform provides you with many options for managing identities. Here are six best practices for securing identities that you can implement today.
- Enable single sign-on. Your users can use the same set of credentials to sign in and access the resources that they need, whether the resources are located on-premises or in the cloud.
- Enforce multi-factor verification for users, especially your administrator accounts. Azure Multi-Factor Authentication (Azure MFA) helps administrators protect their organizations and users with additional methods such as token or phone authentication.
- Turn on Conditional Access. With Azure AD conditional access, you can make automated access control decisions for accessing your cloud apps based on specified conditions. By doing this, every login will be scored to assess its risk and the engine will take actions to reduce it.
- Use Role Based Access Control (RBAC). Restricting access based on the need to know and least privilege security principles is imperative for organizations that need to enforce security policies for data access.
- Enable password management and use appropriate security policies to prevent misuse.
- Limit administrator access to a limited set of users. You can leverage Privileged Identity Management to ensure a just-in-time approach to obtain the required rights.
Implementing these best practices is an essential first step to securing identity in the cloud. Read the Azure Government Security documentation to understand features and variations for Azure Government. For a deeper dive on improving your security posture with Azure, we recommend the following resources:
Look for our next blog on the series next week, focused on improving your IaaS security posture with Azure Government.
We welcome your comments and suggestions to help us improve your Azure Government experience. To stay up to date on all things Azure Government, be sure to subscribe to our blog by clicking “Subscribe by Email!” on the Azure Government Blog.

 Light
Light Dark
Dark
0 comments